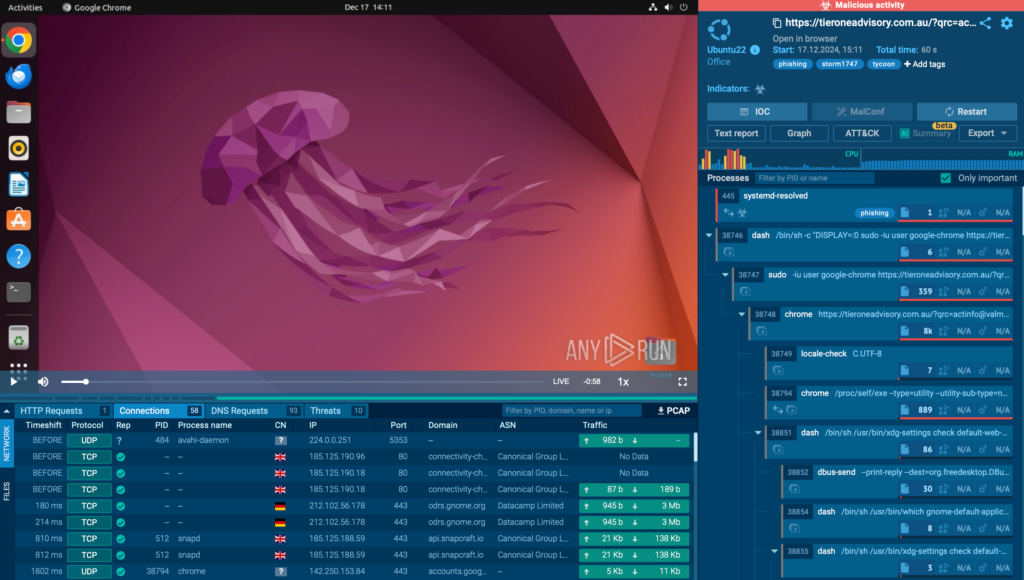
Malware Trends Report: Q4, 2024
Can you believe 2024 has come to an end? As we prepare to step into 2025, we’re excited to share key updates on the cybersecurity front from Q4. The last three months were anything but quiet—new threats emerged, familiar ones evolved, and cybercriminals kept raising the stakes.
At ANY.RUN, we’ve been monitoring these shifts every step of the way. This report pulls together the most significant trends, from the most active malware families to the tactics and techniques shaping cybersecurity.
Let’s jump in and see what this quarter taught us about the intriguing world of malware.
Summary

In Q4 2024, ANY.RUN users ran 1,151,901 public interactive analysis sessions, marking a 5.6% increase from Q3 2024. Out of these, 259,898 (22.6%) were flagged as malicious, and 71,565 (6.2%) as suspicious.
Compared to the previous quarter, the percentage of malicious sandbox sessions rose from 19.4% in Q3 2024 to 22.6% in Q4 2024. At the same time, the share of suspicious sessions grew from 4.3% to 6.2%.
Users collected an impressive 712,151,966 indicators of compromise (IOCs) during Q4, reflecting the heightened activity and complexity of the threats analyzed.
Top Malware Types in Q4 2024
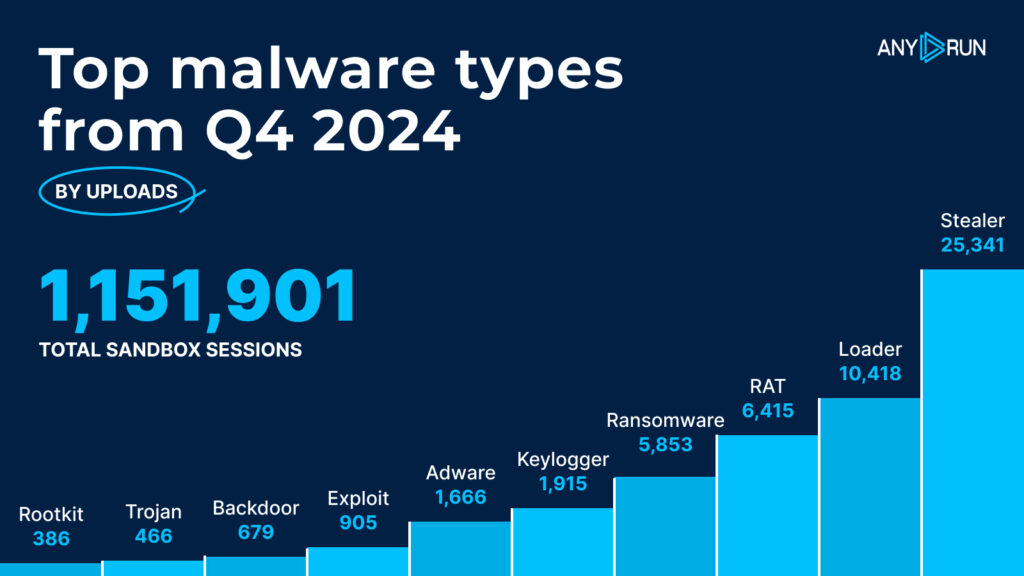
Let’s dive into the most common malware types identified by ANY.RUN’s sandbox in Q4 2024:
| # | Type | Detections |
|---|---|---|
| 1 | Stealer | 25,341 |
| 2 | Loader | 10,418 |
| 3 | RAT | 6,415 |
| 4 | Ransomware | 5,853 |
| 5 | Keylogger | 1,915 |
| 6 | Adware | 1,666 |
| 7 | Exploit | 905 |
| 8 | Backdoor | 679 |
| 9 | Trojan | 466 |
| 10 | Rootkit | 386 |
Top Malware Types: Highlights
Q4 2024 saw significant changes in the most detected malware types compared to previous quarters.
- Stealers took the lead with 25,341 detections, continuing their dominance as the top malware threat. This marks a significant rise from 16,511 detections in Q3, reflecting an increase of 53.5% in Stealer activity. In Q2, Stealers had 3,640 detections, meaning their activity more than doubled from Q2 to Q4.
- Loaders also remained a prominent threat, holding steady in second place with 10,418 detections. This is an increase of 27% compared to Q3, where they were detected 8,197 times. In Q2, Loaders had 5,492 detections, so we’re seeing consistent growth in this malware type across the quarters.
- RATs continued to be a major concern in Q3 and Q4, although their position dropped to third place in both quarters. In Q4, RATs were detected 6,415 times, representing a 10.8% decrease from Q3 (7,191 detections).
- Ransomware saw a slight decrease in Q4, with 5,853 detections, down from 5,967 in Q3, marking a decrease of 1.9%. However, compared to Q2, where ransomware detections were at 2,946, there has still been a clear increase in ransomware activity over the last two quarters.
- Keylogger detections had a notable decrease in Q4, with 1,915 detections compared to 3,172 in Q3. This represents a 39.5% drop from Q3. In Q2, Keyloggers were also detected frequently, but the numbers were lower than what we saw in Q3 and Q4.
A new threat category appeared in the top ten: Adware, which had 1,666 detections in Q4.
Other notable malware types include Exploits (905 detections), Backdoors (679 detections), and Trojans (466 detections). These malware types had a relatively stable presence, with minor fluctuations in the number of detections compared to the previous quarter.
Rootkits, at the bottom of the list with 386 detections, are also showing up more frequently in analyses, though still less common than other types of malware.
Collect Fresh Intel on Emerging Cyber Threats
Make sure to use ANY.RUN’s TI Lookup to collect and enrich threat intelligence on the latest malware and phishing attacks.
The service provides access to a database of over 40 types of Indicators of Compromise (IOCs), Indicators of Attack (IOAs), and Indicators of Behavior (IOBs), from IP addresses to mutexes, extracted from the public samples analyzed in ANY.RUN’s Interactive Sandbox.
With the following query you can find recent samples of Stealer malware uploaded by users in the UK:
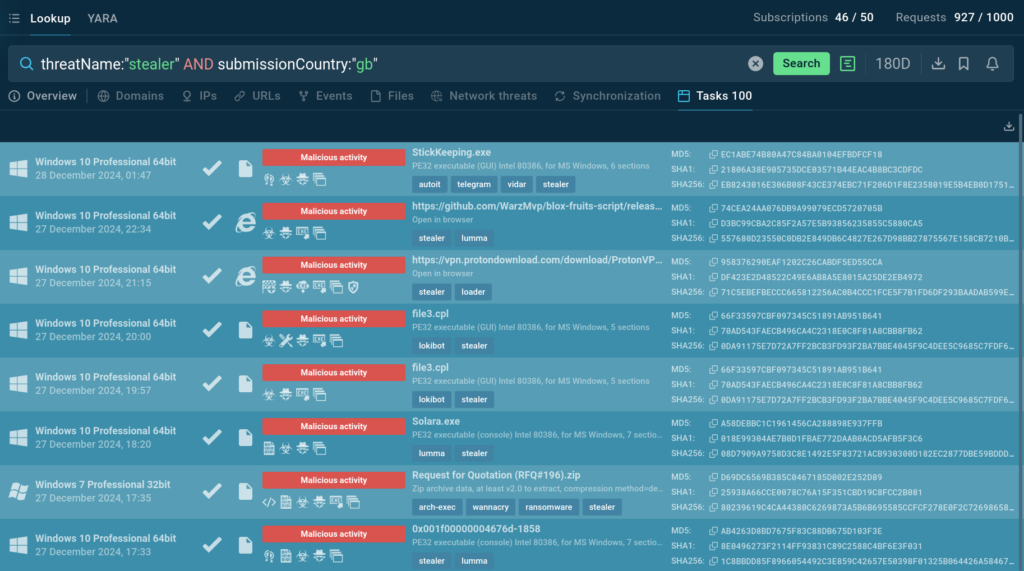
TI Lookup returns dozens of sandbox analyses matching the query that you can explore in detail and gather intel on the current threat landscape.
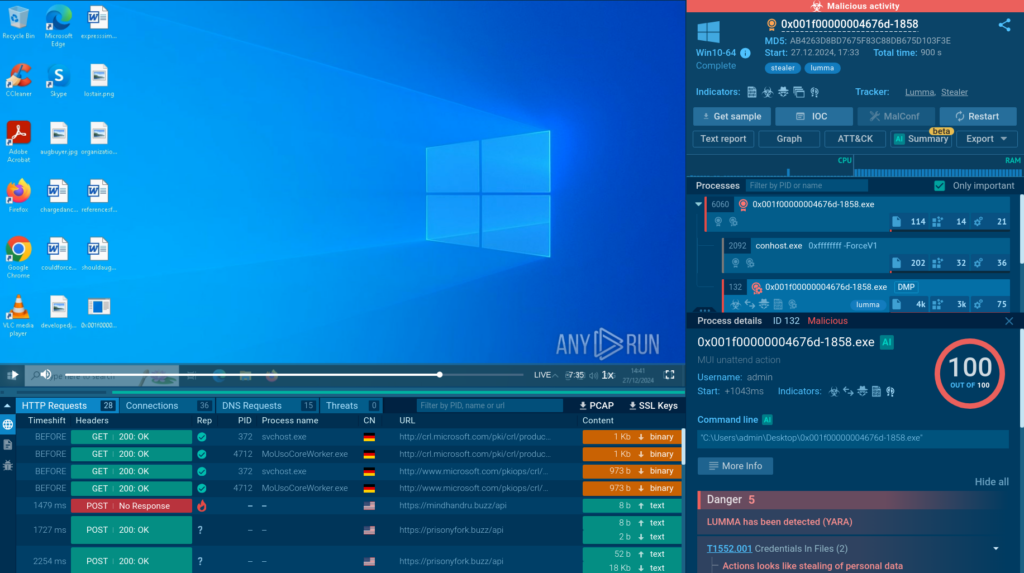
In this session, we can observe the execution process of a Lumma malware sample.
Top Malware Families in Q4 2024

| # | Malware Family | Detections |
|---|---|---|
| 1 | Lumma | 6,982 |
| 2 | Stealc | 4,790 |
| 3 | Redline | 4,321 |
| 4 | Amadey | 3,870 |
| 5 | Xworm | 3,141 |
| 6 | Asyncrat | 2,828 |
| 7 | Remcos | 2,032 |
| 8 | Snake | 1,926 |
| 9 | AgentTesla | 1,906 |
| 10 | Sality | 1,194 |
In Q4 2024, the malware landscape continued to evolve with several shifts in the prevalence of different malware families.
- Lumma maintained its strong position, leading the list with 6,982 detections, showing a significant increase compared to Q3 (4,140 detections).
- Stealc made an impressive jump to second place, with 4,790 detections, up from 2,030 in Q3. This is a 136.3% increase and positions Stealc as a rising threat in the malware world.
- Redline followed with 4,321 detections, a 26.7% rise from Q3.
- AsyncRAT and Remcos showed some decrease in activity, indicating possible shifts in threat actor strategies.
- Xworm, another notable family, saw a substantial rise, reaching 3,141 detections in Q4, up from 2,188 in Q3. This is a 43.7% increase, making Xworm one of the most concerning threats of the quarter.
Snake, which appeared on the list for the first time in Q3, continued its activity in Q4, with 1,926 detections, up from 1,782 in Q3, reflecting an 8.1% increase.
AgentTesla showed a noticeable decrease in activity, dropping to 1,906 detections in Q4 from 2,316 in Q3, which is a 17.7% decline.
Finally, Sality, which had previously been less active, saw a return to the list with 1,194 detections, making it the tenth most detected malware family in Q4.
Phishing Activity in Q4 2024

Phishing activity saw a significant uptick in Q4 2024, with a total of 82,684 phishing-related threats flagged across the ANY.RUN sandbox. This shows just how active cybercriminals were, using phishing tactics to target victims.
Activity by cyber criminal groups:
- Storm1747 led the pack with 11,015 phishing-related uploads, making it the most active group.
- Storm1575 followed with 3,756 uploads, showing strong but more limited activity.
Activity by phishing kits:
- The Tycoon2FA kit dominated the scene, with 8,785 instances of use.
- Mamba2FA came in second with 4,991 detections, reflecting notable activity.
- Evilginx2/EvilProxy made a smaller but significant impact with 573 detections.
- Gabagool had 384 detections, indicating a more niche but active presence.
Top 5 Protectors and Packers from Q4 2024
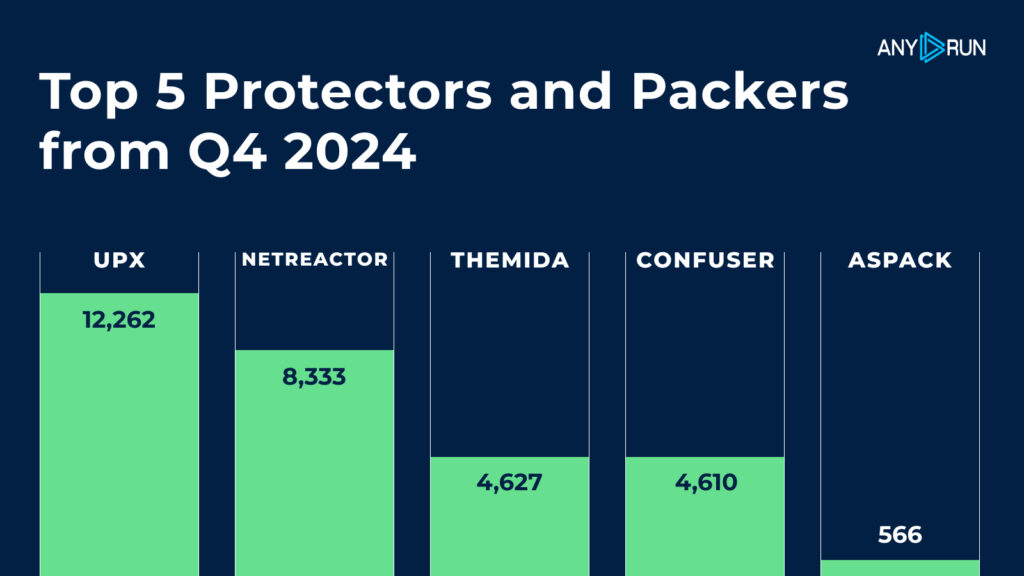
In Q4 2024, the top protectors and packers continued to play a significant role in obfuscating malware to evade detection. Here’s a look at the most common ones:
- UPX: The clear leader with 12,262 detections, making it the most widely used protector/packer.
- Netreactor: With 8,333 detections, it remains a popular choice for malware obfuscation.
- Themida: Used in 4,627 detections, Themida was a key player in malware protection.
- Confuser: Close behind with 4,610 detections, Confuser also stood out for its effectiveness.
- Aspack: The least common in the top 5, but still notable with 566 detections.
These protectors and packers are integral to malware campaigns, helping cybercriminals hide their malicious code and avoid detection.
See detailed guide on unpacking and decrypting malware
Top 20 MITRE ATT&CK Techniques in Q4 2024
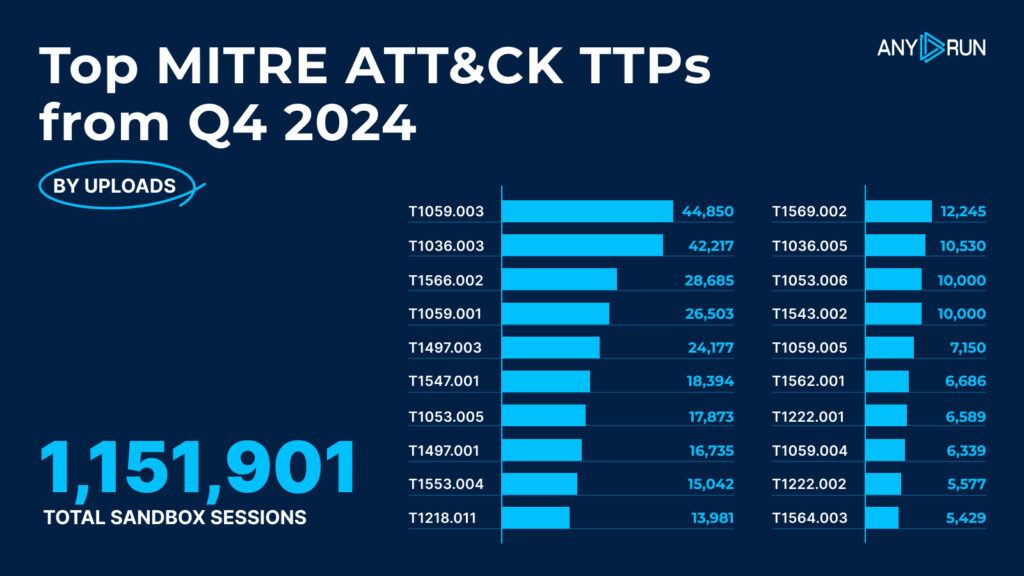
In Q4 2024, several adversary techniques saw a rise in activity, with PowerShell, Windows Command Shell, and phishing techniques dominating the list. Here’s a breakdown of the top 20 techniques observed:
| # | MITRE ATT&CK Technique | Detections |
|---|---|---|
| 1 | Command and Scripting Interpreter: Windows Command Shell, T1059.003 | 44,850 |
| 2 | Masquerading: Rename System Utilities, T1036.003 | 42,217 |
| 3 | Phishing: Spearphishing Link, T1566.002 | 28,685 |
| 4 | Command and Scripting Interpreter: PowerShell, T1059.001 | 26,503 |
| 5 | Virtualization/Sandbox Evasion: Time Based Evasion, T1497.003 | 24,177 |
| 6 | Boot or Logon Autostart Execution: Registry Run Keys/Startup Folder, T1547.001 | 18,394 |
| 7 | Scheduled Task/Job: Scheduled Task, T1053.005 | 17,873 |
| 8 | Virtualization/Sandbox Evasion: System Checks, T1497.001 | 16,735 |
| 9 | Credentials from Password Stores: Credentials from Web Browsers, T1553.004 | 15,042 |
| 10 | System Binary Proxy Execution: Rundll32, T1218.011 | 13,981 |
| 11 | System Services: Service Execution, T1569.002 | 12,245 |
| 12 | Masquerading: Match Legitimate Name or Location, T1036.005 | 10,530 |
| 13 | Scheduled Task/Job: Systemd Timers, T1053.006 | 10,000 |
| 14 | Create or Modify System Process: Systemd Service, T1543.002 | 10,000 |
| 15 | Command and Scripting Interpreter: Visual Basic, T1059.005 | 7,150 |
| 16 | Impair Defenses: Disable or Modify Tools, T1562.001 | 6,686 |
| 17 | System Information Discovery: Application Layer Protocol, T1222.001 | 6,589 |
| 18 | Command and Scripting Interpreter: Unix Shell, T1059.004 | 6,339 |
| 19 | System Information Discovery: Remote System Discovery, T1222.002 | 5,577 |
| 20 | Impact: Data Destruction, T1564.003 | 5,429 |
Top TTPs: Q4 2024 vs Q3 2024
In Q4 2024, the landscape of detected techniques saw a few shifts compared to Q3. Here are the key highlights:
The top three spots for Q4 were claimed by:
- T1059.003, Command and Scripting Interpreter: Windows Command Shell – claiming the top spot, up from the 3rd position in Q3, with a substantial rise in detections (41,384).
- T1036.003, Masquerading: Rename System Utilities – staying strong in 2nd place, though with a slight dip in detections compared to Q3 (41,254).
- T1566.002, Phishing: Spearphishing Link – a significant leap from its previous position, climbing to 3rd with 28,685 detections, marking an increase in phishing-related activities.
Worthy mentions:
- T1059.001, Command and Scripting Interpreter: PowerShell – dropped to 4th place after holding the 2nd spot in Q3, now with 26,503 detections.
- T1497.003, Virtualization/Sandbox Evasion: Time-Based Evasion – although it slipped to 5th place from 4th in Q3, it still saw a notable number of detections (24,177).
- T1547.001, Boot or Logon Autostart Execution: Registry Run Keys/Startup Folder – entering the list in 6th place, showing a steady increase in activity (18,394).
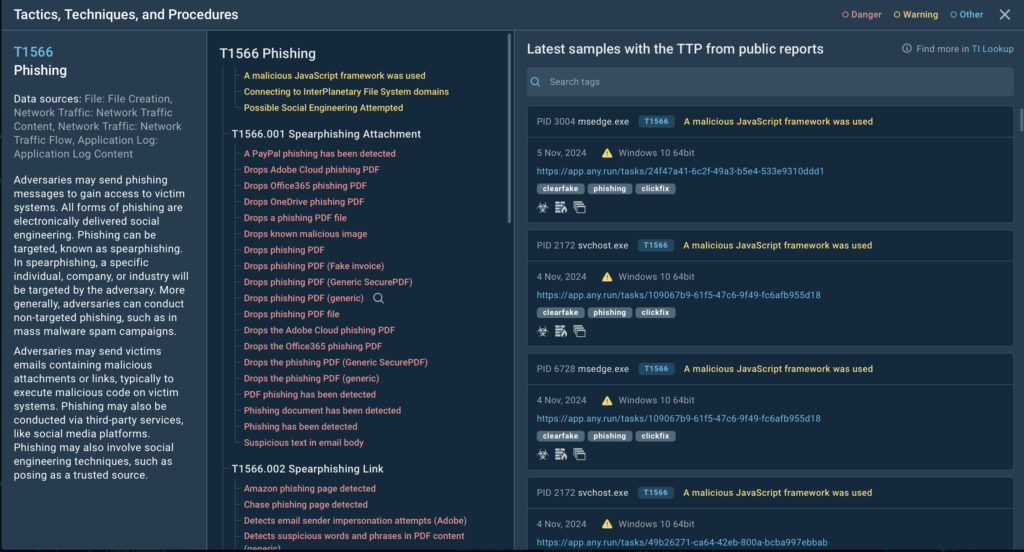
Use TI Lookup’s interactive MITRE ATT&CK matrix which accompanies each TTP with real-world examples of cyber threat samples, analyzed in ANY.RUN’s Interactive Sandbox.
Report Methodology
For this report, we analyzed data from a total of 1,151,901 interactive analysis sessions. This data is drawn from researchers in our community who contributed by running public analysis sessions on ANY.RUN.
These sessions provided valuable insights into the latest trends and activities in cybersecurity, helping us identify key threats and techniques that are currently on the rise.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Get a 14-day free trial of ANY.RUN’s products →
The post Malware Trends Report: Q4, 2024 appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More