Integrate ANY.RUN Threat Intelligence Feeds with Your Security Platform
Editor’s Note: This article was originally published on June 11, 2024, and updated on December 28, 2024.
The ANY.RUN Threat Intelligence Feeds provide data on the known indicators of compromise: malicious IPs, URLs, domains, files, and ports.
The data is collected and pre-processed from public malware and phishing samples analyzed by our community of 500,000 researchers in the ANY.RUN sandbox environment.
How ANY.RUN’s TI Feeds Help Organizations
Cyber Threat Intelligence Feeds from ANY.RUN extend the threat coverage of your SIEM and TIP systems. They provide IOCs of recently seen cyber threats so you can proactively prepare to defend your infrastructure against them, as well as:
- Expand Threat Coverage: Improve system’s ability to detect emerging malware and phishing attacks.
- Improve Incident Response: Enrich incident response processes with contextual data, providing deeper insights into threats and their behaviors.
- Strengthen Security Posture: Ensure proactive defense against new and evolving threats.
- Optimize Threat Hunting: Streamline threat hunting activities, identifying and investigating potential threats more effectively.
Feeds are easy to use. It’s practically a plug and play solution (as long as your team is already using a SIEM or TIP system).
Indicators Provided by ANY.RUN’s TI Feeds
The IOCs include information on malicious IP addresses, domain names, and URLs, enriched with contextual details such as related files and ports.
IP addresses
IP addresses are important for detecting and preventing malicious network activity. They serve as digital markers of cybercriminal operations, often linked to Command-and-Control (C2) servers or phishing campaigns.
By analyzing IP addresses, cybersecurity teams can identify and block malicious sources, trace attack origins and monitor threat patterns.
Domains
Domains are often used as staging points for cyberattacks. They provide a higher-level view of malicious activity, often connecting multiple IPs or malware instances within a single campaign.
ANY.RUN’s TI feeds provide comprehensive information about domains, including all the details available for IP addresses, such as threat names, types, detection timestamps, and related file hashes.
URLs
URL addresses serve as gateways to distribute malware, execute phishing campaigns, or redirect users to malicious content. Their flexibility and ease of use make them a preferred tool for attackers.
By analyzing URLs, cybersecurity teams can uncover attack patterns, block harmful traffic, and prevent unauthorized access to systems and data.
More information on TI Feeds’ structure and additional IOCs — in our blog post.
Key Features of ANY.RUN’s TI Feeds
- Fresh Indicators: Mined from the latest public samples uploaded to our interactive sandbox by a global network of over 500,000 security professionals and updated every few hours.
- Contextual Information: Offer more than just IOCs by providing direct links to sandbox sessions that include memory dumps, network traffic, and events.
- Rigorous Pre-Processing: Advanced algorithms and proprietary technology used for data filtering and validation.
- STIX and MISP Formats: Deliver threat intelligence feeds in the STIX and MISP formats, making it easy for security teams to integrate our data into their existing infrastructure.
Try Demo Sample of ANY.RUN’s TI Feeds
We provide free samples of ANY.RUN’s Threat Intelligence Feeds with data from 6 months ago, so you can test them in your security setting.
Contact us to access the most up-to-date TI Feeds version or make a purchase.
| For ANY.RUN | Have an account registered with a custom domain email |
| For your SIEM/TIP system | Have an account with admin role |
Here are the steps to integrate the demo feeds:
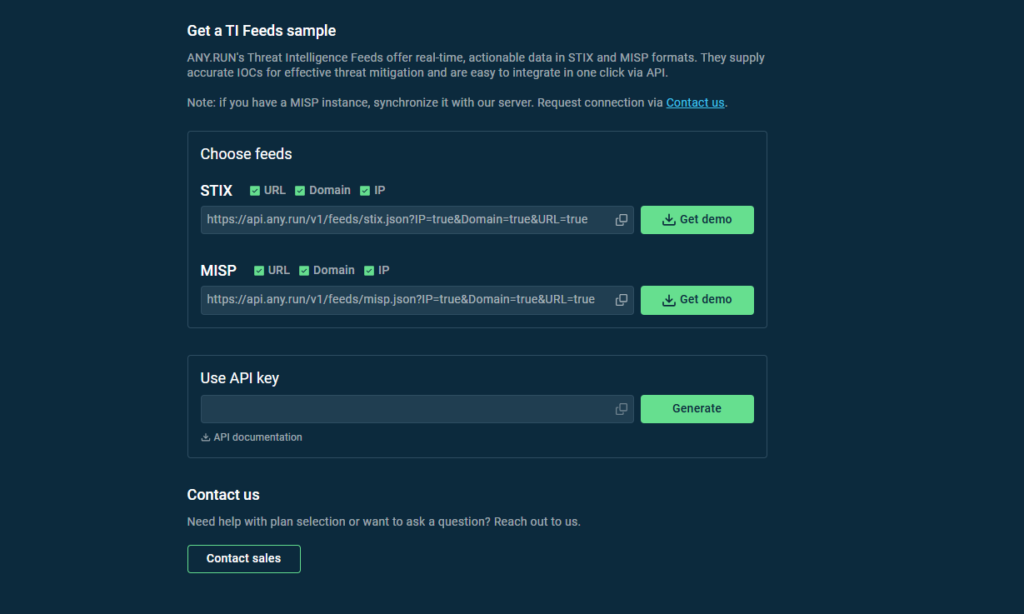
1. First, go to the feeds dashboard.
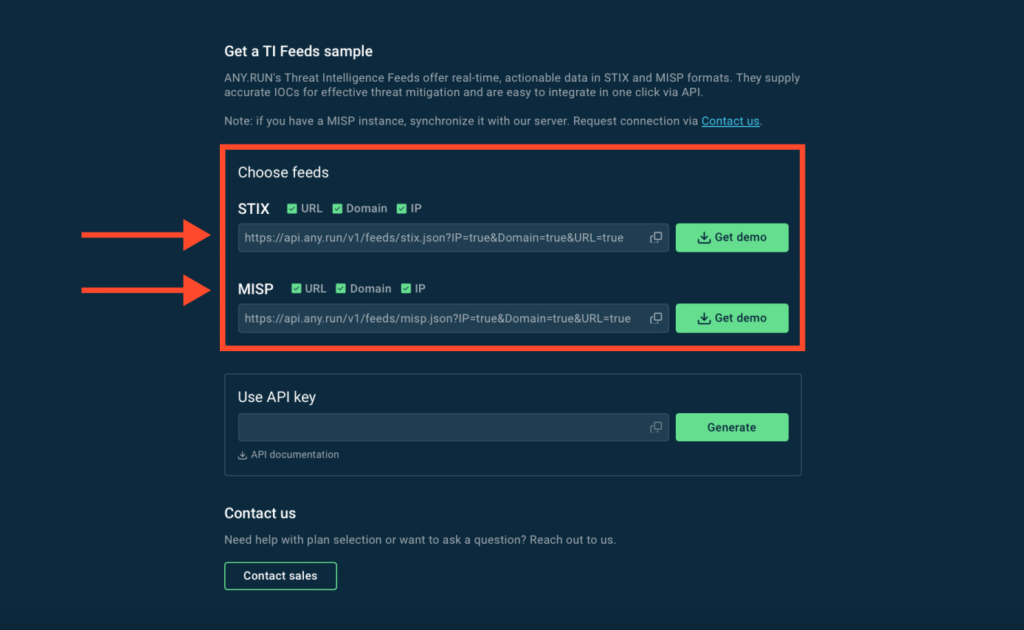
2. Choose which indicators to receive by checking the boxes — URLs, Domains, IPs or any combination of them.
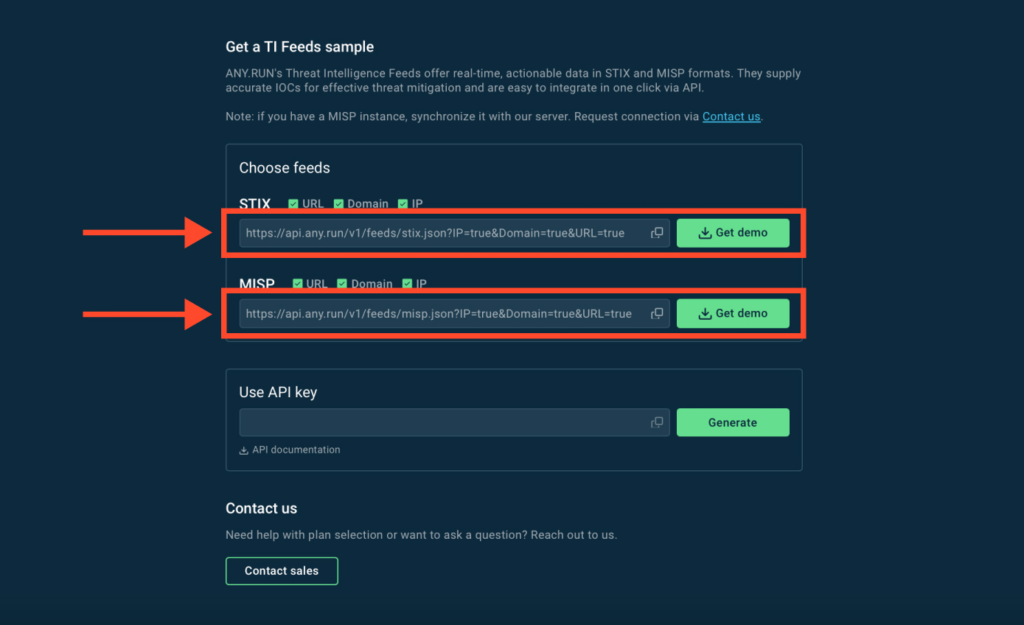
3. Copy the URL and paste it into the threat intelligence feeds section of your SIEM or TIP system. This step depends on your vendor, but generally search for “threat intelligence feeds” and find an input for URL or source.
You can also download a STIX or MISP feeds sample by clicking Get Demo button.
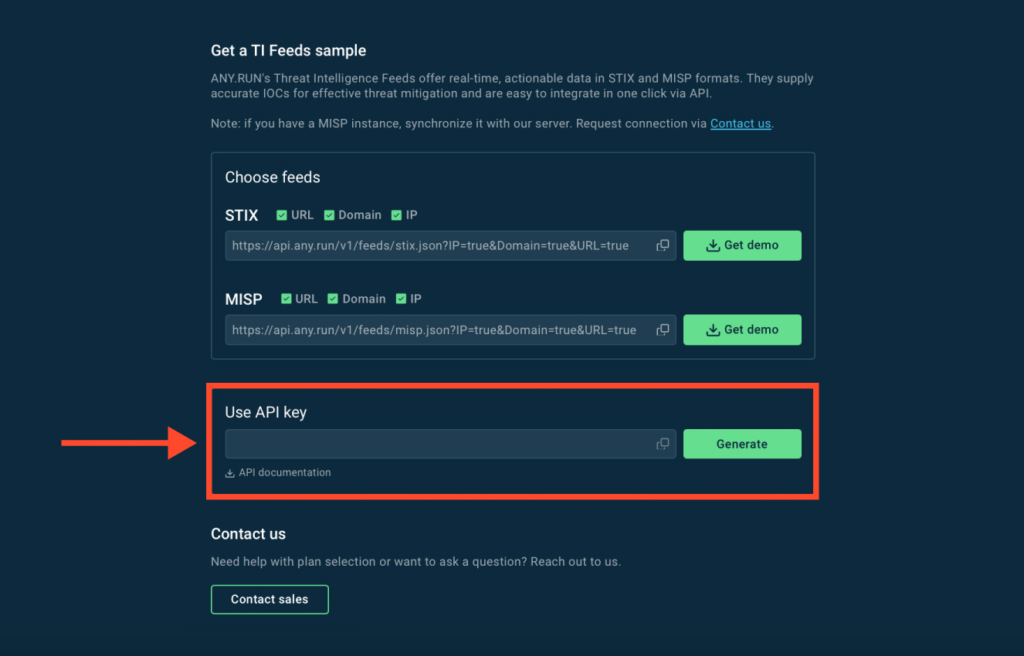
4. Copy the API key and paste it into the API field in the same SIEM/TIP section where you provided the feeds URL.
That’s it! You are now receiving demo threat data from ANY.RUN!
Which vendors can integrate with ANY.RUN?
Our threat intelligence feeds share data in the standardized STIX and MISP formats. This means that you can practically integrate ANY.RUN feeds with any vendor, including popular platforms like OpenCTI and ThreatConnect.
Contact us to get assistance with your integration.
How TI Feeds Support Business Performance
Adding Threat Intelligence feeds to your cybersecurity framework significantly raises the sustainability of your organization.
- Cost reduction: Investing in TI feeds can lead to significant cost savings by preventing data breaches and minimizing the need for reactive security measures.
- Informed decision-making: Quality TI feeds provide critical insights, ensuring that security efforts are focused on the most pressing threats.
- Brand reputation: Early detection of threats reduces the likelihood of incidents that could damage a company’s name.
- Operational efficiency: Integrating CTI feeds with can contribute to better response process, improving mean time to resolution (MTTR).
- Compliance: TI feeds help document incidents, enrich security reports, and meet requirements for frameworks like GDPR, HIPAA, and PCI.
For detailed information on the role of Cybersecurity Threat Intelligence Feeds in improving company’s operational performance, refer to this article.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post Integrate ANY.RUN Threat Intelligence Feeds with Your Security Platform appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More