Release Notes: New Search Operators in TI Lookup, MISP Integration, Multi-admin Support
As we wrap up 2024, we’re excited to share the final release notes of the year, and they’re packed with updates you’re going to love!
This December, we’ve shared some great news with our ANY.RUN community. From new wildcards and search operators in TI Lookup to the launch of our MISP instance and an upgraded Teamwork feature, we’ve been working to make your workflows smoother and more collaborative.
And of course, we’ve expanded our threat coverage to ensure you’re ready to tackle whatever comes next.
Let’s dive in!
New Wildcards and Search Operators in ANY.RUN’s TI Lookup
Searching through massive amounts of cyber threat data isn’t exactly fun. It can be frustrating when small variations in domain names or IP addresses make it hard to connect the dots. That’s why we’ve updated Threat Intelligence Lookup (TI Lookup) with new wildcards and search operators to give you more control and flexibility when crafting queries.
Before this update, TI Lookup allowed you to use the basic operators AND along the wildcard *, which work great for flexible searches.
In December, we’ve expanded this functionality by adding new wildcards and operators to make threat intelligence even more versatile.
What’s new?
- OR: The OR operator broadens your search by including results where at least one of the specified conditions is met.
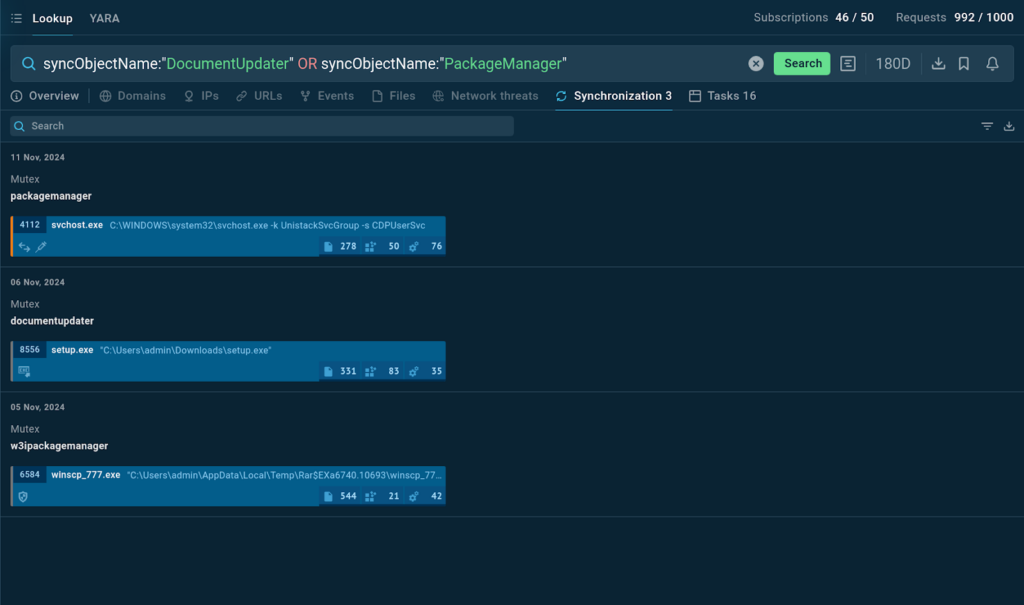
- NOT: The NOT operator excludes results matching specific conditions, narrowing your search to focus on relevant entries.
- Parentheses (): They group conditions to ensure your query processes operators in the correct order, enabling precise, complex searches.
- Question mark (?): Acts as a placeholder for a single character or none, making it perfect for handling variable strings.
- Dollar sign ($): Ensures your search term appears at the end of a string, useful for pinpointing entries with specific endings.
- Caret (^): Makes sure your search term appears at the beginning of a string, ideal for narrowing searches to items starting with specific patterns.
For more details, check out the guide to using wildcards and operators.
MISP Integration: A New Option for Threat Intelligence Sharing
We’re excited to share that in December, we introduced our own MISP instance, providing access to Indicators of Compromise (IOCs) from ANY.RUN’s Threat Intelligence Feeds. This new feature brings even greater collaboration and efficiency to threat intelligence sharing.
MISP (Malware Information Sharing Platform) is a free, open-source tool that streamlines the sharing of threat intelligence, enabling organizations to exchange data, identify compromises, and automate correlations.
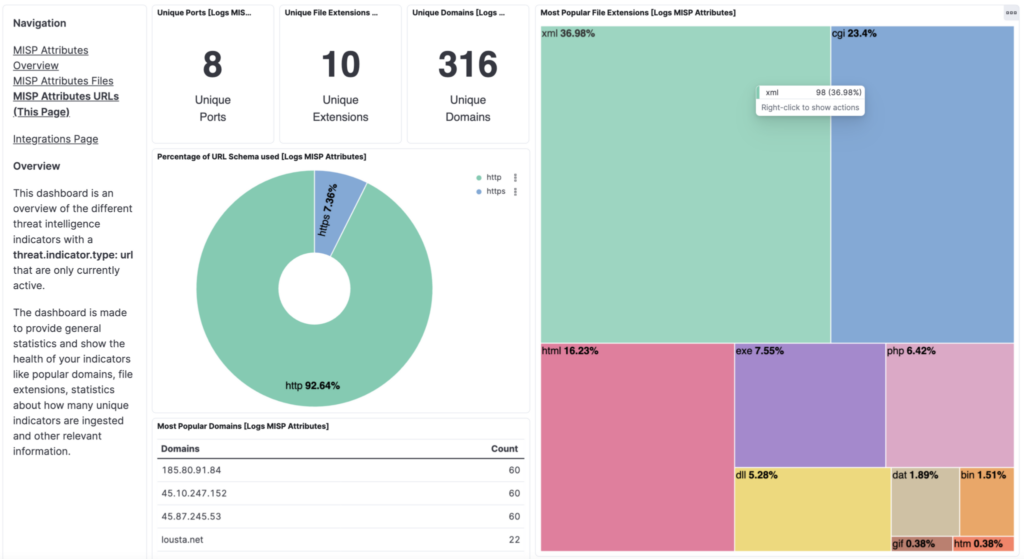
With ANY.RUN’s MISP instance, you can:
- Access TI Feeds: Get real-time streams of malicious IPs, URLs, domains, ports, file names, and hashes from ANY.RUN’s Interactive Sandbox. The IOCs are pulled from different sources, including network activities and malware configurations.
- Integrate with security tools: Connect ANY.RUN’s MISP instance to your SIEM, XDR, or other tools via API.
- Improve threat detection: Enrich your IOCs with ANY.RUN’s data for a clearer understanding of threats.
- Generate IDS rules: Export attributes in NIDS-compatible formats for use in IDS/IPS or NGFW systems.
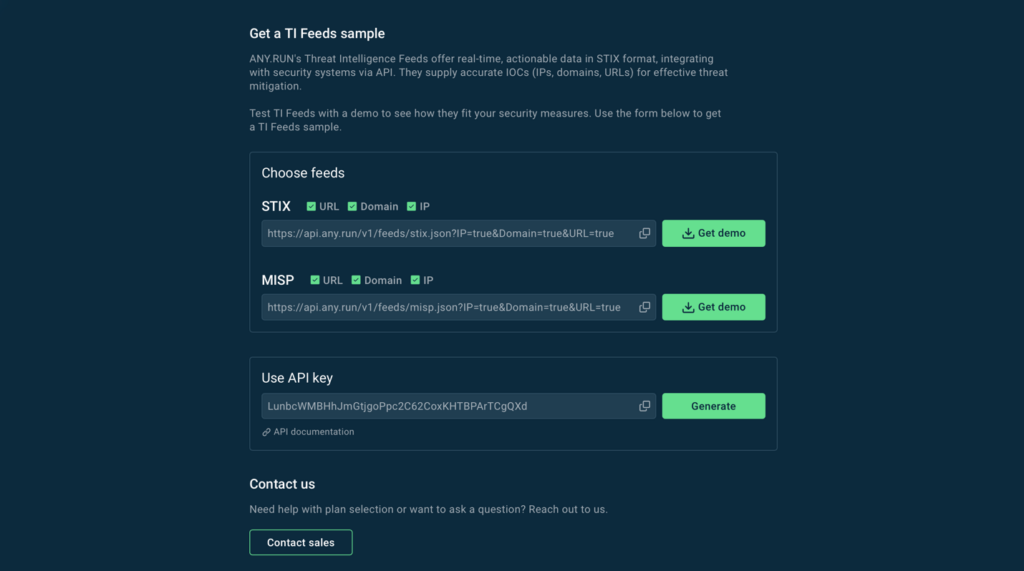
You can test ANY.RUN’s MISP and STIX feeds by getting a free demo sample or contacting us.
New Teamwork Feature: Multiple Admin Support
We’re excited to announce a powerful December update to ANY.RUN’s Teamwork feature, designed to simplify team management and improve collaboration for organizations of all sizes.
Team owners can now assign admin roles to team members, with no limits on the number of admins.
Admins have the following capabilities:
- Enable or disable Single Sign-On (SSO) for the team.
- Invite or remove team members as needed.
- Manage licenses for team members, including access to features like TI Lookup.
Besides, admins can assign or revoke admin rights, ensuring flexible and efficient management.
This update was driven by feedback from our customers, who needed a way to share responsibilities within their teams. Here’s how it can help:
- Delegation: If a team owner is unavailable (e.g., on vacation), responsibilities can easily be handed over to admins.
- Time zone flexibility: Large teams operating in different time zones can now have admins based in various regions, improving responsiveness and workflow efficiency.
How to start using this feature
Team owners can assign admin roles in the Teamwork section under Licenses. Once set up, admins can immediately start managing the team and sharing responsibilities.

Threat Coverage Updates
In December, we expanded our detection capabilities, adding 58 new malware signatures, introducing advanced YARA rules, and further improving our machine learning (ML) models to keep up with evolving threats.
Signatures
We’ve introduced 58 new signatures targeting a diverse range of malware families. Here are some of them:
APT Detection Updates
We’ve enhanced our detection capabilities for several known APT attacks:
- SimpleHelp, BugSleep, and PortStarter are now comprehensively monitored.
New YARA Rules
5 new YARA rules were added this month for more precise detection:
Suricata Rule Updates
This month, we’ve significantly expanded our Suricata rule collection by adding 5,159 new rules, enhancing our detection accuracy across a variety of threats.
These updates include focused detections for phishing kits, such as:
Automated Interactivity Enhancements
We’ve fine-tuned our automated interactivity clicker, making it smarter. These updates mean it’s now even better at interacting with malware samples, accurately simulating how real users might behave.
With these improvements, detecting complex threats just got easier. We made sure you get even more reliable results for your investigations.
About ANY.RUN
ANY.RUN is a leading provider of a cloud-based malware analysis sandbox for effective threat hunting. Our service lets users safely and quickly analyze malware without the need for on-premises infrastructure. ANY.RUN is used by organizations of all sizes, including Fortune 500 companies, government agencies, and educational institutions.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Get a 14-day free trial of ANY.RUN’s Interactive Sandbox →
The post Release Notes: New Search Operators in TI Lookup, MISP Integration, Multi-admin Support appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

