How to Set up a Windows 11 Malware Sandbox
As Windows 10 approaches its end-of-life (October 2025), organizations are facing the need to adjust their security infrastructure to be better aligned with Windows 11. A malware sandbox, an isolated environment for analyzing malicious files and URLs, is a key tool for this transition.
Here are the benefits of deploying a Windows 11 sandbox and how you can do it.
What is a malware sandbox?
A malware sandbox is an isolated virtual environment designed to safely analyze cyber threats by detonating, observing, and interacting with them.
This controlled setting allows cybersecurity professionals to understand the behavior of malware post-infection, including file modifications, network calls, and registry changes.
A malware sandbox helps organizations and individual researchers to:
- Safely explore malicious files and URLs to validate threat alerts or proactively identify cyber threats.
- Observe detonation of malware and phishing attacks in real time to see how they are carried out in a live system.
- Replicate specific network and system environments to assess the potential impact on the existing infrastructure.
- Extract indicators of compromise from malware samples to enhance threat detection capabilities.
- Intercept and analyze command and control communications to gather crucial IOCs.
- Study malware behavior in depth to uncover tactics, techniques, and procedures (TTPs) to respond to security incidents or prepare for future attacks more effectively.
Which sandbox to choose? Built-in, on-premises, cloud-based
When it comes to choosing your sandbox, there are several options you can consider. Let’s focus on the three main ones.
Built-In Sandbox Feature Included with Windows 11
Windows 11 provides built-in sandbox functionality completely for free. This tool works well for quick checks, such as opening malicious links received via phishing emails or downloading and running suspicious files.
A limitation of this type of sandbox is its inability to provide verdicts on detonated malicious content or log system and network activities. This can make it difficult to accurately assess the threat level of evasive and complex malware. There are also no reports generated after the analysis.
These aspects make the built-in Windows sandbox an unsuitable option for professional use.
On-premises Windows 11 Sandbox
For more advanced analysis, organizations can opt for building their own sandbox environment, configured to their specific needs. Virtualization software like VirtualBox can be used here. Yet, this approach is generally recommended only if you need to reverse-engineer malware source code or analyze it with custom tools.
There are also a several things to take into consideration:
- Complex Setup: Requires technical expertise to set up and configure.
- Potential Risks: Misconfiguration can lead to malware escaping the sandbox and infecting the host system.
- Resource-Intensive: Can be demanding on system resources.
Check out this guide on how to set up your own sandbox environment.
Cloud Malware Sandbox with Windows 11 Support
For professional malware analysis, a cloud sandbox is the best choice. These services offer all the benefits of virtualization software but with much less tinkering and setup, making it easier to gather deep insights. There’s also no chance to misconfigure something and let the malware escape the sandbox’s confines and infect the host.
The ANY.RUN sandbox is a tool that lets you configure and deploy a fully-interactive Windows 11 environment in seconds. It also provides you with the ability to engage with the system just like on a standard computer: launch programs, download attachments, browse web pages, and type.
Some malware families may rely on specific tools and mechanisms present in certain OS versions; running them on the wrong version may not trigger their malicious actions. That is why, apart from Windows 11, ANY.RUN provides other operating systems, including Windows 7, 10, and Ubuntu, letting you switch between them with ease.
Benefits of ANY.RUN’s Interactive Sandbox:
- Quick and Easy Setup: Simply upload your file or link and start the analysis process in seconds.
- Real-time Insights: Get an in-depth view of malicious activities, including network events, registry changes, dropped files, script execution, as they occur.
- Interactivity: Perform user actions and see how threats respond in a live system.
- Comprehensive Reporting: Collect detailed reports on analysis results, such as indicators of compromise (IOCs), malware families config info, and other actionable info.
- VM Customization: Configure VM settings, enabling custom VPN, MITM Proxy, FakeNet, and other features for targeted investigations.
- Privacy Control: Choose between public and private analysis based on data sensitivity.
- Team Management: Invite, manage, and remove team members, with options for temporary access and productivity tracking.

How to Set up a Windows 11 Sandbox
Let’s demonstrate how you can quickly get started with ANY.RUN’s Interactive Sandbox.
Step 1: Upload a Sample
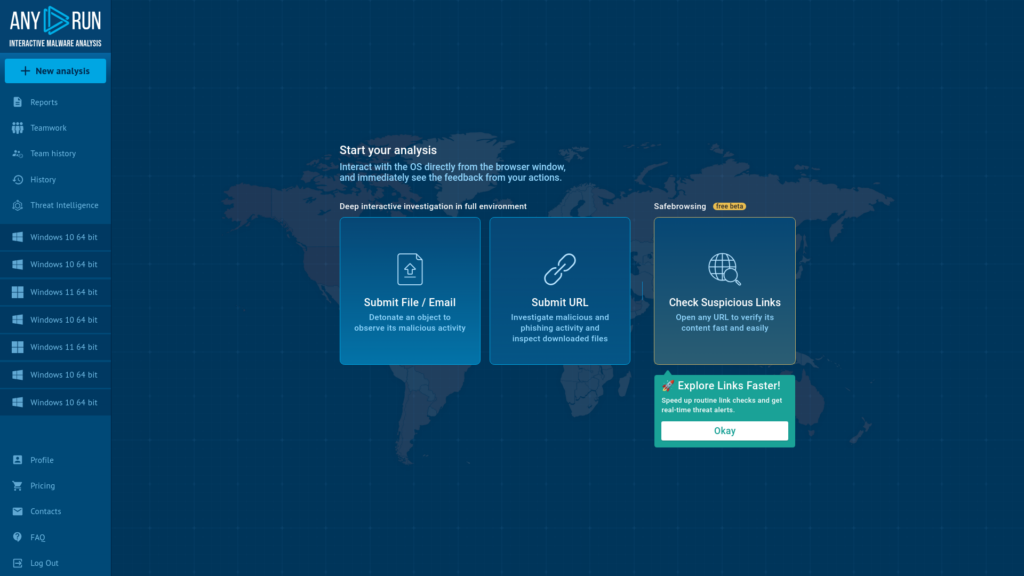
First, create an account or log in and choose your upload option: a file or URL.
As an example, let’s upload a .bin file to the service.
Step 2: Configure the VM
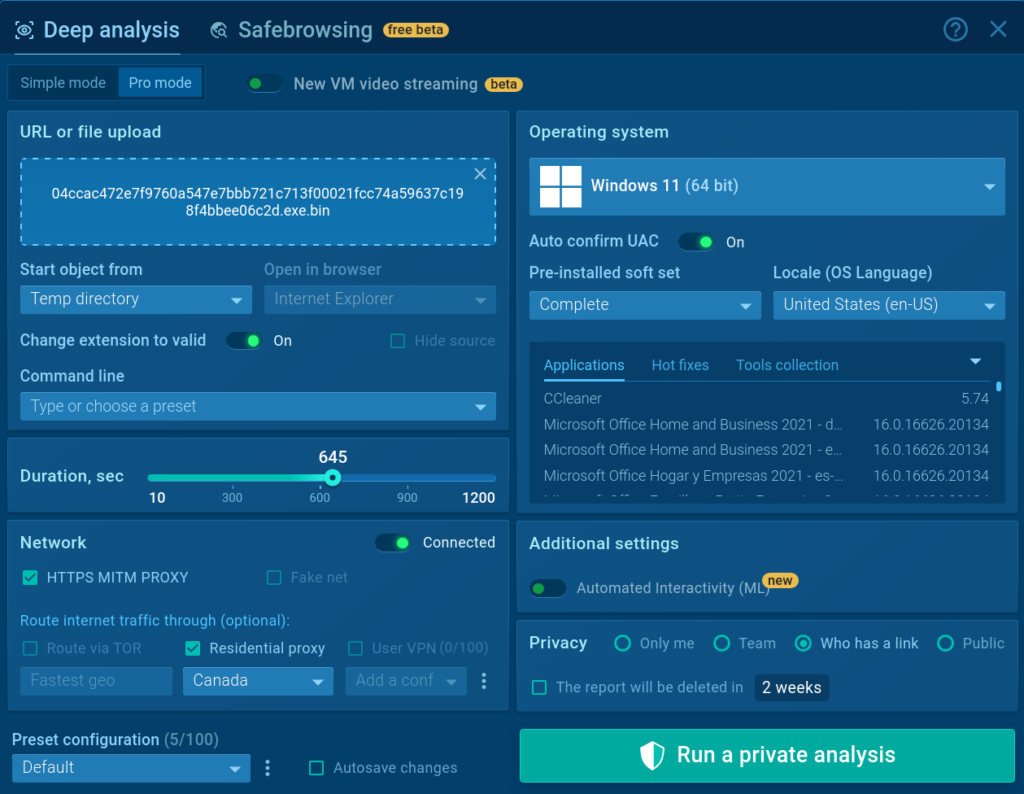
Once we submit the sample, we’ll be able to customize the analysis environment to fit our needs. Check out the ultimate guide to the ANY.RUN sandbox to learn more about the features available in the setup window.
For now, let’s select Windows 11 from the list of operating systems, set the privacy mode of the session, and run the analysis.
Step 3: Analyze the Threat
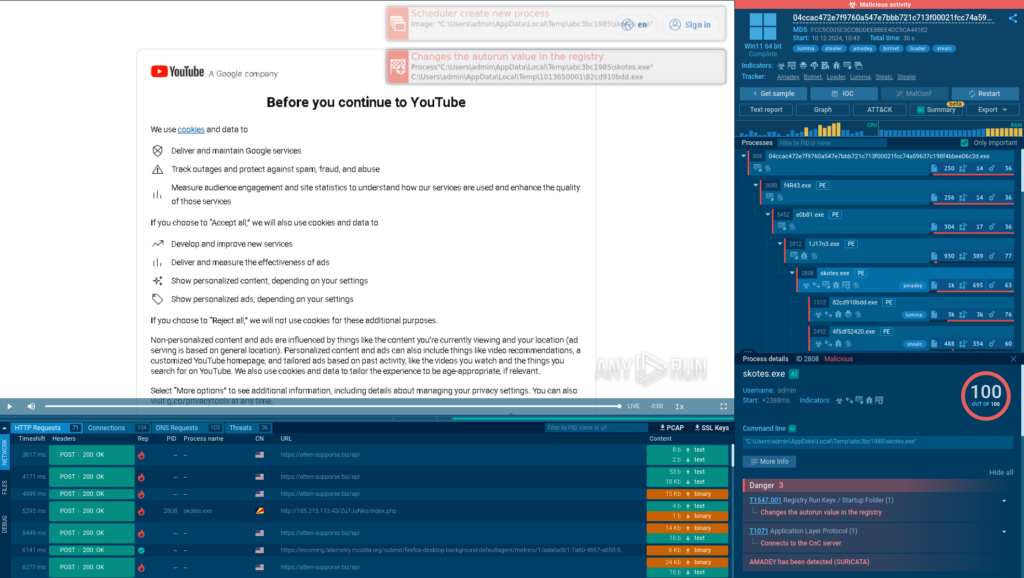
Once the session starts, the sandbox detonates the sample, allowing us to see how the system gets infected with the Amadey malware.
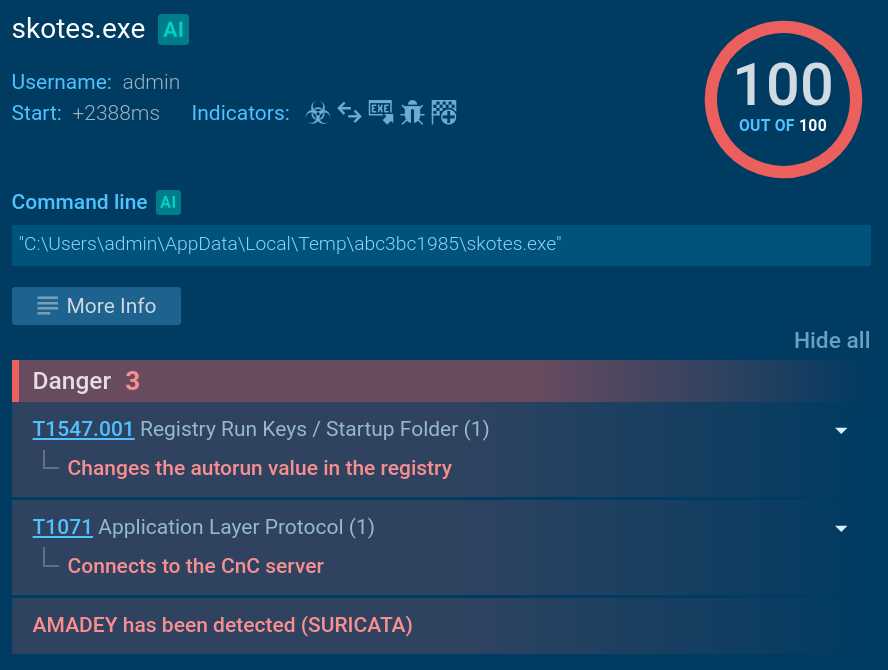
Thanks to the Process Tree, we can discover that after the initial infection, Amadey continues to deploy additional malware, Lumma and Stealc.
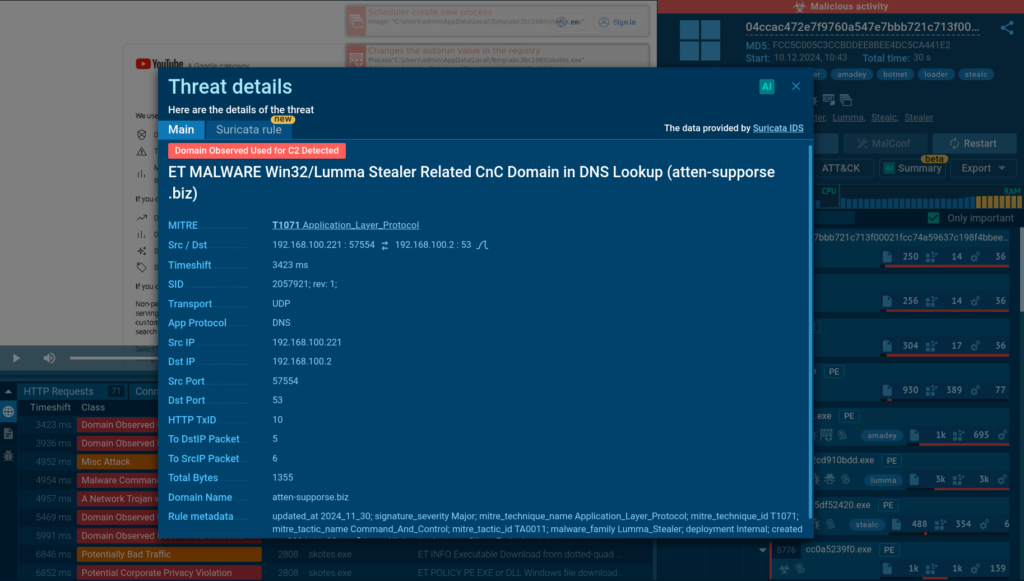
Once these threats gain foothold on the system, they connect to their command and control (C2) servers, receive commands from threat actors, and begin to exfiltrate stolen data.
Conclusion
By providing a safe and isolated environment for analyzing malicious files and URLs, a malware sandbox helps enhance threat investigations and improve security. Organizations transitioning to Windows 11 need to utilize a reliable sandbox solution to effectively examine emerging malware and phishing attacks.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Get a 14-day free trial to test all features of ANY.RUN’s Interactive Sandbox →
The post How to Set up a Windows 11 Malware Sandbox appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

