Explore MITRE ATT&CK Techniques in Real-World Samples with TI Lookup
We’re excited to announce the latest update to Threat Intelligence (TI) Lookup. The enhanced home screen now integrates all techniques and tactics of the MITRE ATT&CK matrix, along with relevant malware samples and signatures.
Let’s dive into how these updates can transform your workflow and help you tackle threats with greater confidence.
Redesigned Threat Intelligence Dashboard
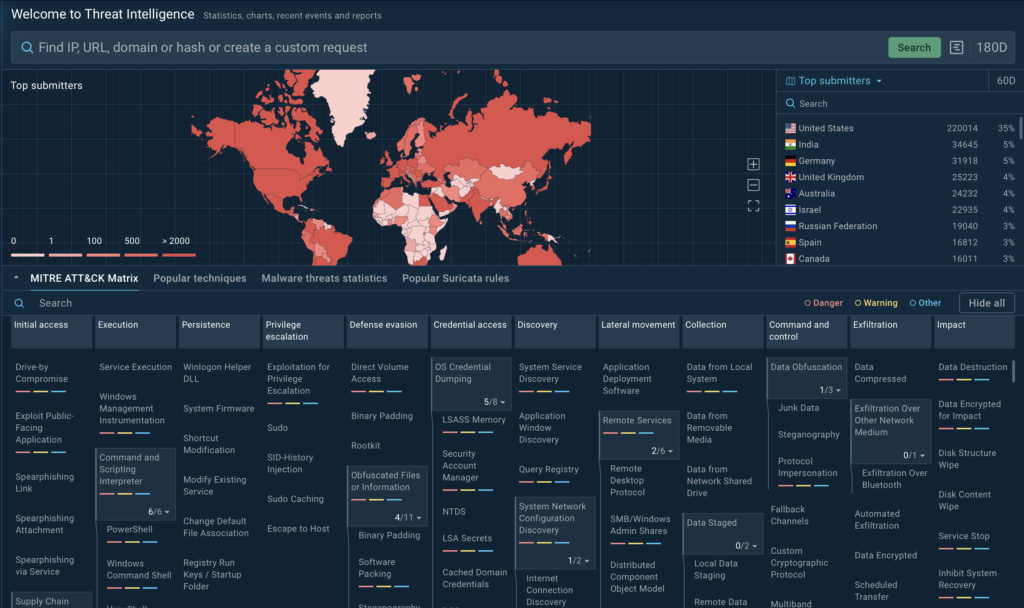
The centerpiece of the updated Threat Intelligence home screen is the MITRE ATT&CK matrix, neatly organizing tactics and techniques into a clear, actionable layout.
But here’s where it gets really exciting: The matrix is interactive and lets you explore actual malware samples tied to each technique. This bridges the gap between theoretical knowledge of attack patterns and practical insights into how those patterns are used in real-world attacks.
The new home screen is designed to be super functional for anyone working with malware, whether you’re a malware analyst, an incident responder, a threat researcher, or just someone curious about how malware operates.
Making the MITRE ATT&CK Matrix Actionable
One of the core goals of this redesign was to turn the MITRE ATT&CK classification into a working tool for analysts. Instead of just showcasing popular techniques, the matrix now:
- Covers all techniques we detect—not just a subset.
- Links techniques to detection data and real-world examples.
- Helps analysts identify patterns and connections across incidents.
This update takes analysts beyond just understanding the techniques and tactics. It helps them put that knowledge into action.
They can see how specific techniques have been used in real attacks, spot the malware families tied to certain behaviors, and fine-tune their detection rules to better defend against similar threats in the future.
How to Use the Interactive MITRE ATT&CK Matrix
With the new home screen, all techniques and tactics are displayed clearly. Clicking on any technique opens up a wealth of information and analysis samples related to it, including its sub-techniques.
The updated TI Lookup now includes filtering options for MITRE ATT&CK matrix techniques to help users prioritize threats:
- Red (danger): High-risk techniques requiring immediate action.
- Yellow (warning): Moderate-risk techniques for ongoing analysis.
- Blue (other): Low-risk or less urgent techniques.
Users can refine their view by choosing to hide or display specific categories using the button next to the labels.
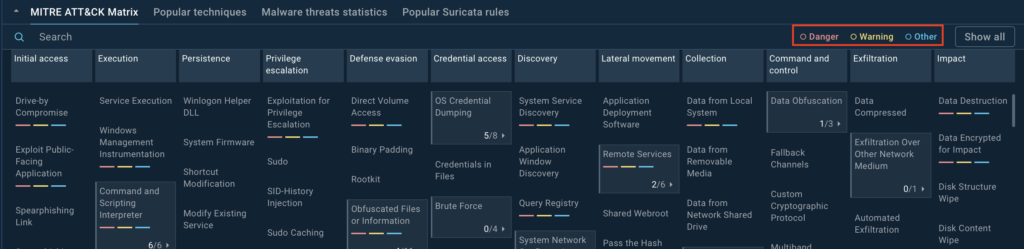
Here’s an example of how the redesigned TI Lookup can be used to explore real-world malware scenarios. Let’s take a closer look at the samples related to spearphishing links.
In the Initial Access section of the MITRE ATT&CK matrix, you’ll find Phishing (T1566), which includes sub-techniques like spearphishing.
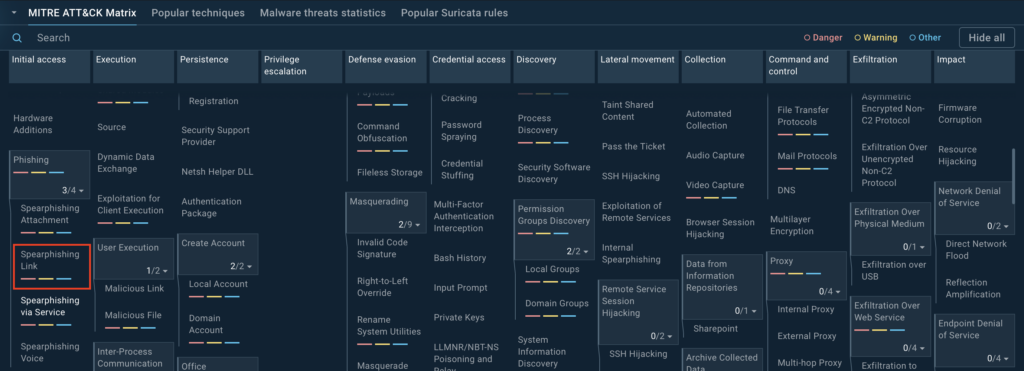
Clicking on Phishing brings up a new tab with detailed information, including:
- An overview of Phishing and its popular sub-techniques, such as spearphishing links, spearphishing attachments, and more.
- Insights into related processes and threats.
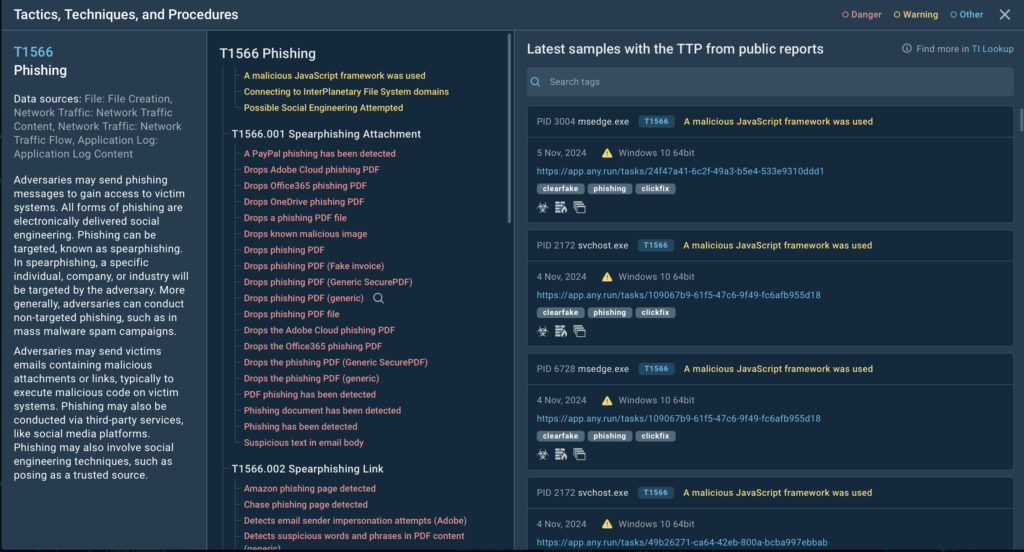
For example, under the Spearphishing Links sub-technique, you’ll see signatures pulled from actual analysis sessions.
These might include:
- A QR code containing a malicious URL,
- A potential phishing attempt leveraging Freshdesk abuse,
- Suspicious URLs identified in real-world samples, and much more.
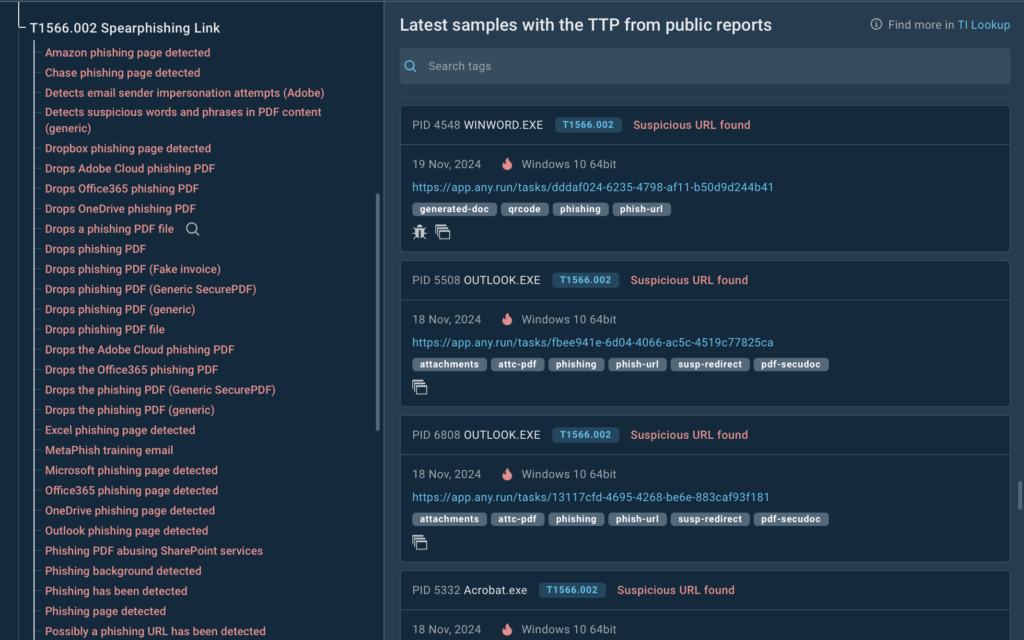
When you select a technique, sub-technique, or a specific signature, the service will show relevant samples along with links to corresponding sandbox sessions where the selected TTP was identified.
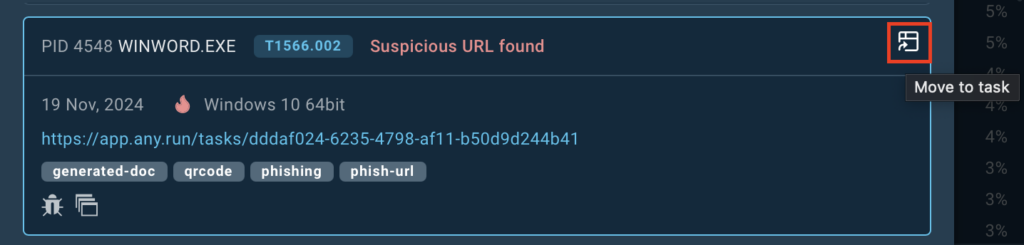
With one click, you can jump into ANY.RUN’s sandbox to observe the behavior of the malware in action and analyze the attack’s overall structure.
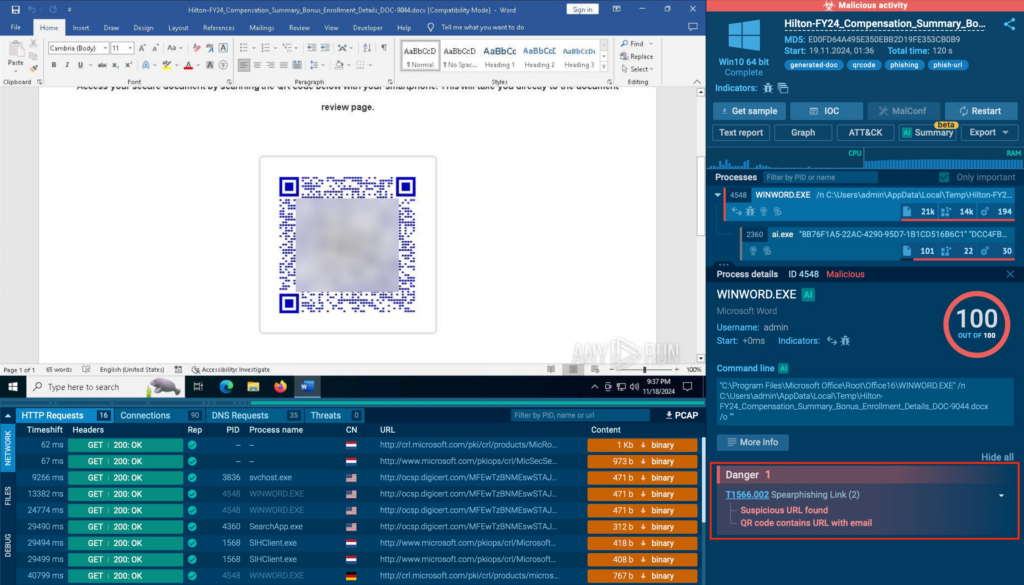
If you want to dive deeper and gather Indicators of Compromise (IOCs) for your analysis, there are two ways to do so.
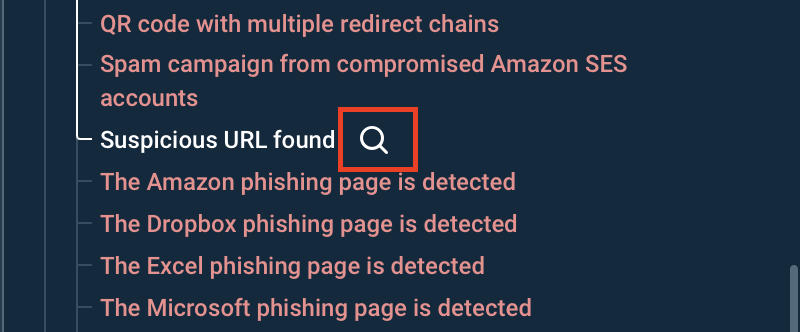
First, you can use the search icon next to each threat to instantly uncover additional details, such as domains, IPs, URLs, files, and other relevant context tied to the selected technique.
Alternatively, by clicking on TI Lookup in the upper-right corner of the tab, you’ll be redirected to the dedicated TI Lookup search page.
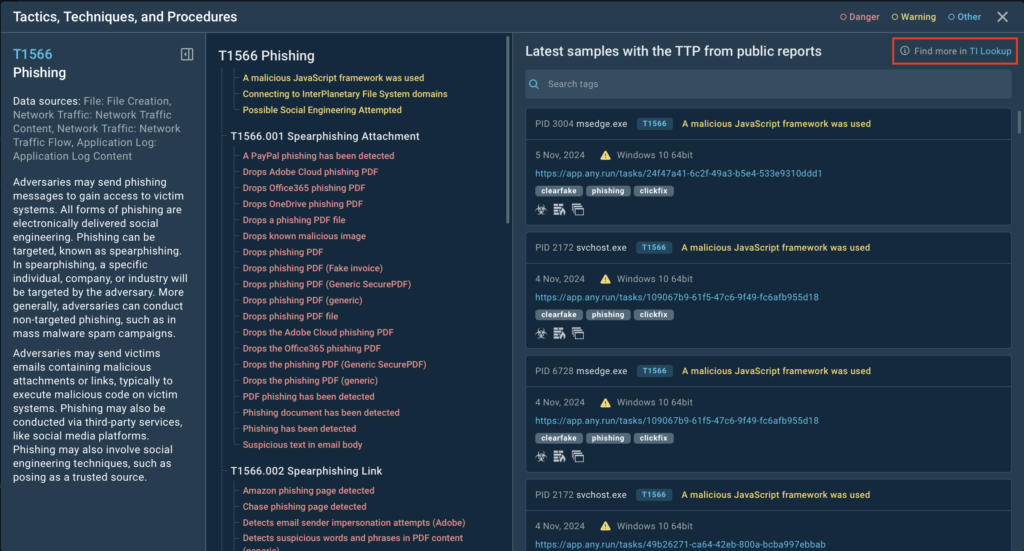
Here, you can refine your search and explore a wealth of actionable intelligence. TI Lookup is designed to provide everything an analyst needs in one place, comprehensive data about specific techniques, behavior patterns, malware families, and their associated IOCs, IOBs, and IOAs.
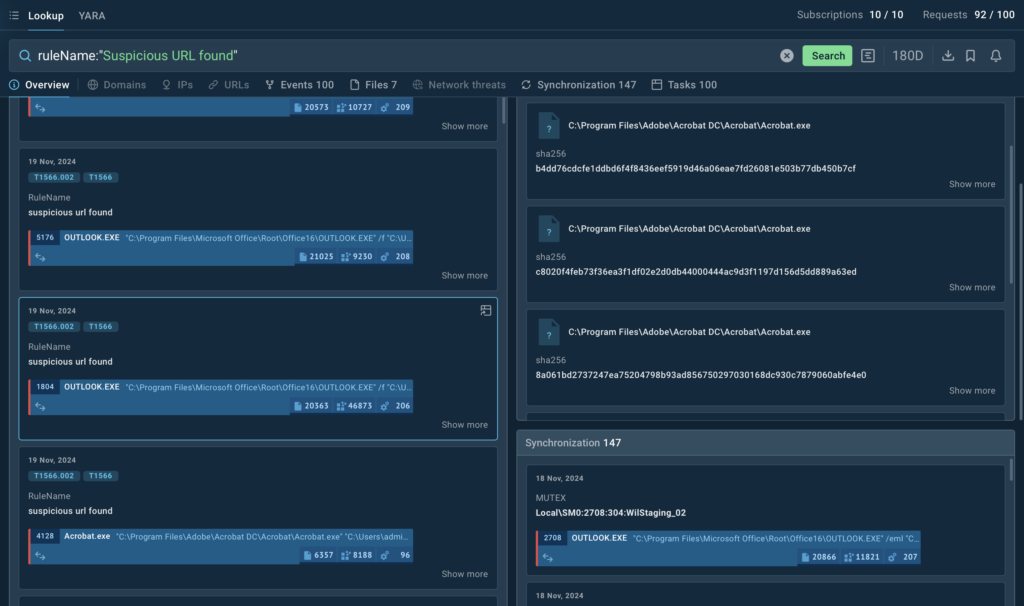
This new workflow not only makes it easier to understand the processes behind a specific technique but also provides the context needed to develop better strategies for combating similar threats.
For instance, by analyzing spearphishing links in-depth, you’ll gain insights into the methods attackers use to trick victims and the types of payloads delivered. Armed with this knowledge, you can:
- Create detection rules tailored to phishing tactics.
- Enhance your defense mechanisms to block similar attacks in the future.
- Build detailed reports for stakeholders, complete with real-world examples and actionable recommendations.

Conclusion
Whether it’s phishing, persistence techniques, or lateral movement, TI Lookup provides the tools you need to dive deep into the data and make informed decisions. With the redesigned home screen, the service is now even more useful for security analysts and researchers, as it helps them easily find samples where specific TTPs were used.
Ready to see it in action? Head over to Threat Intelligence Lookup and start exploring!
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Request free trial of ANY.RUN’s products →
The post Explore MITRE ATT&CK Techniques in Real-World Samples with TI Lookup appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

