ANY.RUN’s Upgraded Linux Sandbox for Fast and Secure Malware Analysis
At ANY.RUN, we’re always working to improve our services, and this time, we’ve focused on making our Linux sandbox even better. We’ve fine-tuned every detail to ensure it runs as smoothly and reliably as our Windows environment.
From bug fixes to feature enhancements, our Linux sandbox is now more powerful and stable than ever, giving you a seamless experience when analyzing Linux malware.
What’s Updated in ANY.RUN’s Linux Sandbox?
We’ve packed our latest update with powerful new features and improvements that upgrade both performance and usability.
Here’s what’s new in our Linux sandbox and how these enhancements benefit you:
Stable Chrome browser by default: We’ve integrated a stable version of Chrome as the default browser for Linux environments. This ensures smoother, faster browsing and more reliable interaction with suspicious websites during your analysis sessions.
Improved process tree performance: We’ve eliminated the lag that previously occurred when navigating the process tree. Now, you can explore process details without any delays, making malware behavior analysis much more efficient.
Additional file uploads for Linux: This means that you can now upload files in real time while an analysis session is running, enabling a more dynamic investigation process. Instead of having to restart or set up a new session for each file, you can simply upload more files during the current session.
File events tracking: This feature allows users to monitor and log every action the malware performs on files within the Linux sandbox environment. For example, if the malware creates, modifies, deletes, or moves files, those actions are now captured and presented in the analysis report.
Now you can get a clearer view of how the malware interacts with the file system, providing deeper insights into the malware’s behavior and making it easier to trace malicious activities.
Clipboard feature: A new clipboard function has been introduced, allowing you to copy and paste content directly within the sandbox. This small addition significantly improves workflow and efficiency during interactive sessions.
Improved Locale (OS Language) selection: We’ve enhanced the Locale (OS Language) choice feature in the Linux sandbox, making it more reliable and error-free. Now, during configuration, you can easily select the desired locale from the dropdown menu, ensuring that the operating system language is set correctly for your analysis session.
This improvement is crucial because malware often behaves differently depending on the system’s language settings. For example, some malware may only activate in specific locales, or attackers may target systems based on region-specific characteristics. By choosing the correct locale, you can replicate real-world scenarios more accurately.
Internal stability improvements: We’ve also carried out other optimizations to ensure the Linux sandbox runs as smoothly and reliably as our Windows sandbox.
These improvements include removing various bugs, making performance tweaks, and implementing backend updates. While these changes might not be immediately visible, they play a crucial role in enhancing the overall stability and efficiency of the Linux sandbox, giving you a seamless experience when analyzing malware.
Let’s Analyze Mirai Malware in Linux Sandbox
To see the updated Linux sandbox in action, let’s dive into how one of the most infamous Linux malware threats, Mirai, can be analyzed in just a few steps.
It’s easy, fast and straightforward:
1. Choose the right option for analysis
To begin the analysis, we need to choose one of the options:
Upload the suspicious file: You can explore a variety of formats, including shell scripts, ELF executables, tarballs, and more. Even common files like Word documents, which might carry hidden malware targeting Linux, can be checked thoroughly.
Copy and paste the suspicious link: Safely browse shady websites, whether they’re suspected of hosting malware or trying to pull off phishing scams.
2. Configure the sandbox settings
After selecting the option you need, you can adjust the sandbox settings. A key step is choosing “Linux OS” from the list of operating systems in the dropdown menu. This ensures the analysis session will run on a Linux system, providing the right environment for your testing.
Ready? Hit that “Run analysis” button and start interacting with the file or link to check if it’s malicious.
In our case, we’re running a malware analysis session with Mirai:
3. Start analyzing the Linux malware
After launching the analysis, the Linux sandbox will display tags related to the threat at hand.
Just take a glance at the top-right corner of the screen. In our case, the sandbox provides tags “mirai” and “botnet”.
Once you finish the analysis, the sandbox will show the final verdict, letting you know if the file or link is malicious or safe.
If you want more details about the specific malware, you can click on the links provided by the Tracker located next to the indicators. This will take you to the malware tracker, where you can read a detailed description of the malware, including its origin, execution analysis, distribution methods, and much more.
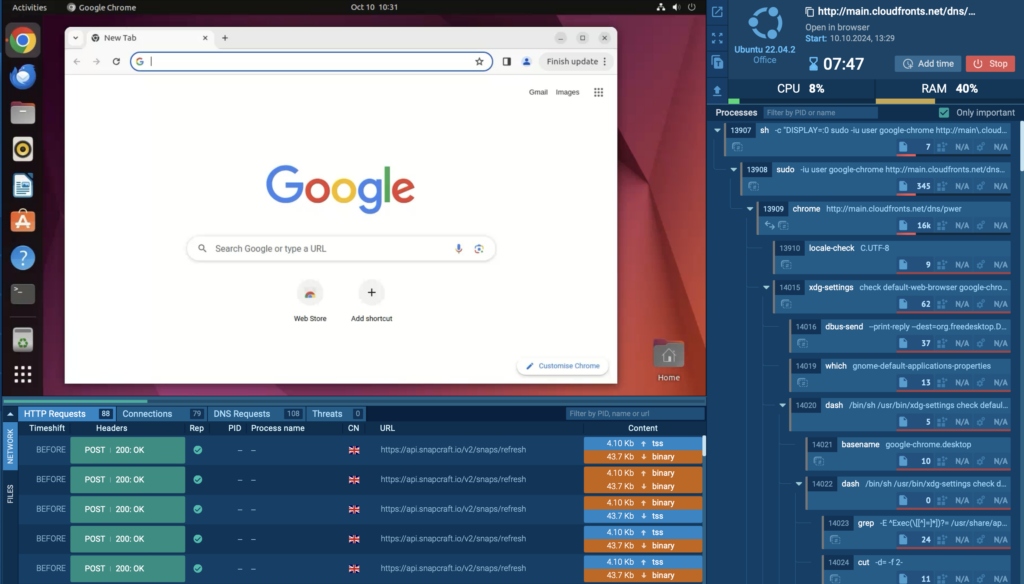
Detailed malware processes
Next, over on the right side, you’ll find the process tree, showing all the parent PIDs and their child PIDs. This gives you a clear view of how malware behaves across processes. Want more details? Just click on any process, and you’ll get a deep dive into its activity.
Network analysis details
Below the virtual machine, you’ll also see a breakdown of all the network activity—split into HTTP requests, connections, DNS requests, and detected threats. This info is key for understanding the malware’s behavior.
For example, in our analysis session with Mirai malware, we can see how it uploads ELF files designed for specific system architectures.
By piecing together these insights, you get a comprehensive look at how the malware operates, making it easier to investigate and respond to potential threats.
Collection of IOCs and network reputation
For further analysis of the malware, you can easily gather all the IOCs (Indicators of Compromise) linked to the task by clicking the IOC button on the right side of the screen.
No need to jump between tabs—everything you need is collected in one place, making it quicker and easier to manage.
Plus, before each IOC, you’ll find a network reputation indicator that lets you know whether the item is whitelisted or flagged as malicious, so you can prioritize it in your investigation.
MITRE ATT&CK tactics and techniques
ANY.RUN’s Linux sandbox also includes the MITRE ATT&CK Matrix framework, which is super helpful for understanding the techniques and tactics used in malware attacks.
Simply click the ATT&CK button, and you’ll be redirected to a new page showing all the techniques employed in the specific malware activity.
MITRE ATT&CK tactics and techniques used for Mirai malware attack
For example, in our Mirai malware analysis, one of the tactics used by the attackers was leveraging wget to download additional content—highlighting just how attackers manipulate common tools for malicious purposes.
Process graph
ANY.RUN’s Linux sandbox offers a process graph that visually maps out the entire malware attack, showing every action the malware takes from start to finish. This graph gives you a clear, easy-to-understand view of the attack’s flow—how it starts, what files are accessed, and what processes are executed.
This feature is especially useful for more complex malware, where multiple actions happen simultaneously. You can zoom in on individual processes or view the bigger picture to get a complete understanding of how malware spreads and what it’s trying to accomplish.
Here is the process graph of our analysis, showing how Mirai infiltrates the system:
Mirai malware analysis text report
During our interactive analysis of Mirai malware in the Linux sandbox, we saw just how detailed the investigation can get. From process trees to network interactions, the sandbox provides a deep dive into every aspect of the malware’s behavior.
If you need to collect and review all this information later, you can easily do so by clicking the “Text Report” button in the upper right corner. This feature gathers all the critical details into one report, combining everything from the process graphs to the full scope of network activity for further analysis.
Learn more: Malware Analysis Report in One Click
Why Use ANY.RUN’s Linux Sandbox?
ANY.RUN’s Linux sandbox is built for both security professionals and beginners who need a reliable and fast environment to analyze malware targeting Linux systems.
Real-time analysis: Watch malware activity live and react to the behavior instantly.
Full isolation: Safely inspect files and URLs without risking your main system.
Comprehensive threat detection: Handle all Linux malware types, including backdoors and crypto miners.
Easy setup: Start a session in just a few clicks—no complex setup required.
Interactive environment: Interact directly with the malware and see its impact in real-time.
Centralized IOCs: All indicators of compromise are gathered in one spot for easy access.
Secure Cloud: Everything runs safely in the cloud—no need for local software.
Detailed report: Receive a comprehensive analysis report after each session, including all critical findings.
Experience ANY.RUN’s Full Power with a Free Trial
Unlock the full potential of ANY.RUN with advanced features to elevate your malware analysis:
Windows 11 VM
API access and integration with Splunk and OpenCTI
And more
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
The post ANY.RUN’s Upgraded Linux Sandbox <br>for Fast and Secure Malware Analysis appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More