Release Notes: Safebrowsing, Private AI Assistant, Splunk Integration, and more
Welcome to ANY.RUN‘s monthly updates, where we share our team’s achievements over the past month.
September has been a productive month at ANY.RUN, packed with exciting new features and improvements. We’ve launched Safebrowsing, a powerful tool that lets you safely check suspicious URLs in an isolated browser.
In addition to that, we’ve integrated with Splunk, enhanced our sandbox capabilities, and rolled out new signatures and YARA rules to help you strengthen your security.
Let’s break down what’s new in ANY.RUN step by step.
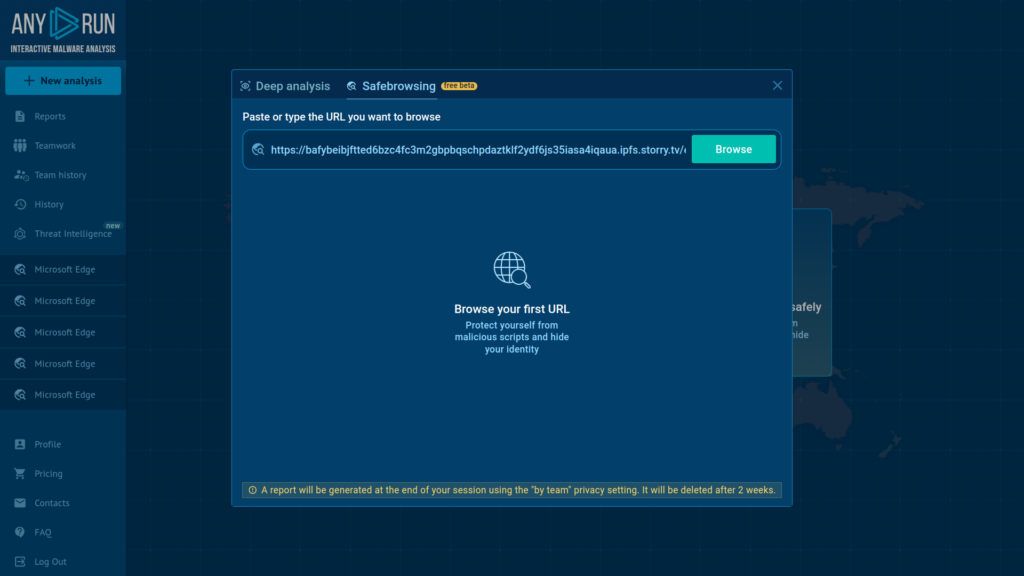
Safebrowsing for Quick URL Checks
We’ve released Safebrowsing, a new tool that allows ANY.RUN users to safely analyze suspicious URLs within a fully interactive, isolated browser. It is a quick and secure way to explore websites and verify potentially malicious content without putting your local system at risk.
You can interact with suspicious links in real time, detect threats using our proprietary technology, and receive detailed reports, including Indicators of Compromise (IOCs) and network traffic analysis.
Now available in free beta for all ANY.RUN users, it adds a new layer of security to your daily operations.
New Integration with Splunk
In September, ANY.RUN officially launched an integration with Splunk. It brings access to our Interactive Sandbox and Threat Intelligence Lookup directly in the Splunk SOAR environment.
With this integration, Splunk users can now analyze potentially malicious files and URLs in ANY.RUN’s sandbox and enrich their investigations using TI Lookup with comprehensive threat intelligence from TI Lookup—all without leaving Splunk.
Key features:
Comprehensive threat intelligence: Query ANY.RUN’s threat intelligence database directly from Splunk SOAR using the ‘get intelligence’ action.
Automated malware analysis: Automatically detonate files and URLs in ANY.RUN’s sandbox as part of a Splunk SOAR playbook.
Detailed reporting & IOC extraction: Quickly retrieve detailed reports and extract IOCs for further threat investigation and response.
Advanced threat hunting: Perform complex queries against ANY.RUN’s threat intelligence database to search for file hashes, IP addresses, domains, and more.
AI Assistant for Private Sandbox Sessions
We’ve improved the sandbox’s AI capabilities by replacing the ChatGPT assistant with our own private AI model. Now you can access AI-powered explanations in both public and private analysis sessions, without worrying about your data going to any third party.
This private AI model is especially useful for those new to the cybersecurity field.
It breaks down complex data quickly, helping you better navigate your analysis and extract useful insights.
Security Training Lab
In September, we launched Security Training Lab, a new program designed to equip future cybersecurity professionals with practical, hands-on skills.
Universities often struggle to keep their curricula up to date, but Security Training Lab bridges the gap between theory and real-world practice.
Through in-depth modules and access to ANY.RUN’s tools, students gain valuable experience in detecting and responding to real threats.
Key advantages of Security Training Lab include:
30 hours of academic content: Including written materials, video lectures, and interactive tasks.
Access to ANY.RUN: Students and instructors use real-world tools to analyze threats.
Practical learning: Hands-on experience with real cyber threat samples.
Network Detections Update
In September, we added 459 new Suricata rules, of which 382 are dedicated to phishing detection.
This significant increase comes from closely monitoring the activity of threat actor Storm-1575, leading to the identification of two primary tools currently used by this group.
New Signatures
In September, we added a total of 9 new signatures. Here are some highlights:
Stealc signature for mutex detection
Razr signature for .raz file extension
SFX Dropper signature
Alucard ransomware
Tgbdownloader adware
Xmrig mutex and file drop detection
Hawkeye ransomware detection
Scheduled task creation via Registry
EFI boot file modification
YARA Rules Update
We’ve added 5 new YARA rules to detect various malware threats:
Megatools downloader
Goldeneye ransomware
Diablonet detection
Pown ransomware
AutoIT scripts detection
Additionally, we’ve updated the YARA rule for Lumma, enhancing the detection mechanism for this threat.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
Detect malware in seconds
Interact with samples in real time
Save time and money on sandbox setup and maintenance
Record and study all aspects of malware behavior
Collaborate with your team
Scale as you need
Request free trial of ANY.RUN’s products →
The post Release Notes: Safebrowsing, Private AI Assistant, Splunk Integration, and more appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More