What is Spearphishing: Definition, Techniques, Real-world Example
Roughly 70% of malware incidents are a result of social engineering, with spearphishing being a common method. Let’s learn more about this phenomenon and discover:
What is spearphishing and what makes it so dangerous
Common techniques used in spearphishing attacks
Tools you can employ in your defense strategy
An example of a real-world spearphishing attack
What is spearphishing?
It is a targeted form of phishing attack where the adversary focuses on a specific individual or organization. Unlike generic phishing, spearphishing is often more sophisticated and uses personalized information to make the attack more convincing.
What are the main goals of spearphishing?
The most common objectives are delivering a malicious payload, but other goals can be pursued, too:
Disclosure of sensitive information: obtaining personal, financial, or business-critical information for fraudulent use or selling on the dark web.
Unauthorized system access: capturing credentials for unauthorized access, potentially leading to further compromise within a network or system.
What makes spearphishing dangerous?
It is highly targeted and tailored to each victim, making it more challenging to defend against compared to generic phishing attacks.
Spoofing genuine connections of the victim, impersonating business associates, or tailoring a message around the receiver’s interests — all of these factors make spearphishing even more challenging to recognize than common phishing.
For example, attackers may impersonate a high-ranking executive within a company, sending an email to an employee requesting urgent payment or confidential information. The email will appear genuine, leaving little chance for the victim to recognize an attack.
Another tactic attackers sometimes use is gaining access to an actual business associate’s email account. Then, they will lead the recipient to believe that the email is from a trusted contact, but in reality, it contains malware.
Spearphishing and phishing compared
We’ve created this table show what aspects make spearphishing so destructive and why you should be concerned about this potential threat:
Aspect
Spearphishing
Phishing
Targeting
Specific targeting: focuses on specific individuals or organizations, making the attack more dangerous as it can exploit known vulnerabilities or personal connections.
General targeting: mass-targeting approach makes it less dangerous per individual, as it’s less likely to exploit personal weaknesses.
Personalization
Highly tailored: utilizes personal or professional information, making it more convincing and dangerous as it appears more legitimate.
Generic: little or no personalization makes it less dangerous as it is often less convincing.
Research required
Extensive research: the detailed research increases danger by enabling precise targeting, exploiting specific vulnerabilities.
Minimal research: lack of research on individual targets makes it less effective and dangerous.
Success rate
Higher success rate: customization leads to more successful attacks, posing greater risk.
Lower success rate: The broader approach results in a lower success rate, making it less dangerous on an individual level.
Difficulty to detect
Harder to detect: relevance and customization make detection more challenging, increasing danger.
Easier to detect: generic nature often makes it more noticeable, reducing danger.
Potential impact
More damaging: focused targeting can lead to significant harm to the individual or organization, making it more dangerous.
Less damaging: typically less damaging on a per-victim basis, as the attack is not personalized to exploit specific weaknesses.
Who are the most likely targets of spearphishing?
Medium-sized businesses and enterprises. These attacks take a lot of effort to prepare, which is why adversaries typically pursue high-risk, high-reward targets.
Within these organizations, the most vulnerable individuals to spear-phishing are often those with access to critical information but may lack adequate training or awareness regarding cybersecurity.
These might include:
Senior executives: they often have access to critical company information but might not be as tech-savvy or aware of the latest security threats.
Human resources and administrative staff: these individuals typically have access to personal employee data and might be targeted due to their role in internal communications.
IT staff: although usually more aware of threats, their high-level access makes them a prime target.
New or temporary employees: They may not be as familiar with organizational policies or may lack training in cybersecurity awareness.
It is likely that adversaries will blur the border between phishing in spearphishing in the near future and start targeting a wider range of victims. This likely shift is the result of new AI tools which simplify spearphishing attacks.
What are some common spearphishing techniques?
Spearphishing employs targeted techniques to deceive recipients and achieve specific objectives:
Personalized emails: leveraging information about the victim to craft convincing emails, often to deliver malware or solicit sensitive information.
Using compromised accounts: taking over legitimate accounts to send emails that seem trustworthy, with the objective of spreading malware or gathering further credentials.
Website spoofing: creating fake websites that resemble legitimate ones to capture login credentials, leading to unauthorized access to sensitive systems.
Social engineering: manipulating individuals through phone calls or direct interaction to obtain personal or financial information.
Targeting mobile devices: sending SMS or leveraging mobile apps to install malicious software or gather data directly from the user’s device.
What tools can help an organization defeat these techniques? We’ve made a table listing some useful resources that organizations can utilize to protect against spearphishing:
Resource type
Description
Examples or providers
Online interactive sandboxes
Environments to safely analyze and investigate suspicious files and links.
Training platforms
Tools and platforms for employee training on recognizing spearphishing.
KnowBe4, PhishMe, Wombat Security Technologies
Email security solutions
Systems to authenticate and filter email, blocking potential spearphishing.
Mimecast, Barracuda, Proofpoint, Cisco Email Security
Multi-Factor Authentication
Technologies providing additional authentication layers.
Microsoft Authenticator, Google Authenticator, Duo
SIEM Tools
Tools for monitoring and analyzing network behavior.
Splunk, IBM QRadar, ArcSight
Privileged Access Managements systems
To manage and limit user access rights.
CyberArk, Thycotic, BeyondTrust
Analyzing a real-world spearphishing attack in a malware sandbox
What is a malware sandbox
A malware sandbox is a service that offers a safe isolated environment for exploring malware and phishing attacks. ANY.RUN provides a cloud-based sandbox that lets you interact with threats just like you would on your own computer.
The interactivity is particularly useful when analyzing spearphishing, as it makes it possible to manually explore the entire chain of attack, from the initial email or URL and to the final phishing page or malicious payload.
Let’s see how the ANY.RUN sandbox works using the example of a malicious email.
Analysis of a spearphishing attack
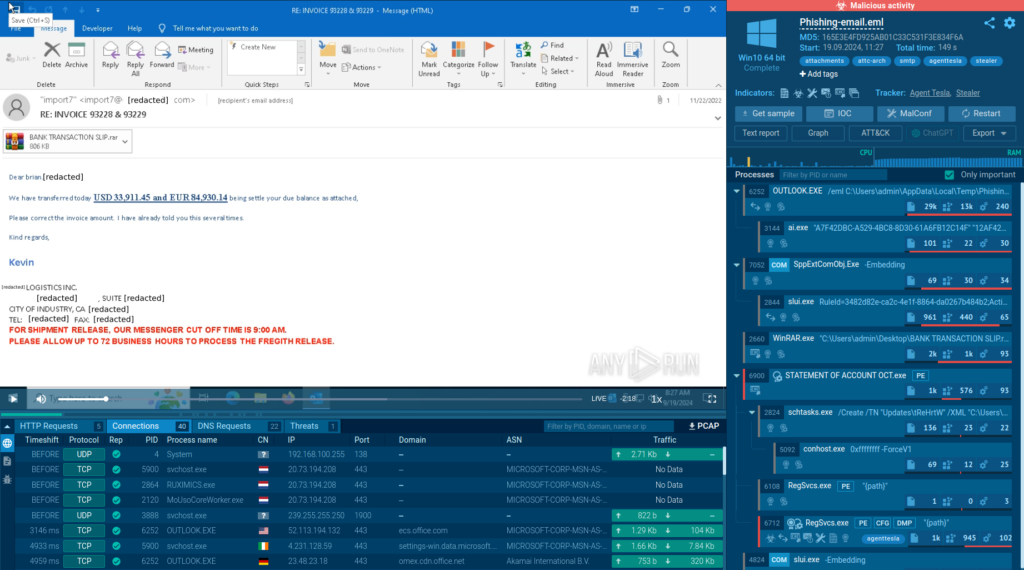
Consider this analysis session.
We start with a suspicious email targeting a particular person. Attackers often mimic the style and design of official emails from trusted organizations like banks, postal services, and manufacturers to make their phishing attempts appear more legitimate.
In our case, the message claims that the sender had transferred a certain amount of money and asks the recipient to review an attached archive, which supposedly contains an invoice, and verify the amount.
Thanks to ANY.RUN’s interactivity, we can download the attachment and open it directly inside the sandbox with no problem.
Inside the downloaded archive, there is a file named “STATEMENT OF ACCOUNT”. This is a common technique used by cyber criminals, who often disguise malicious files with legitimate-sounding names.
The fact that the file is an executable also raises suspicion, as this type of file is not typically sent in business correspondence. Yet, using a sandbox, we can safely extract and launch it to observe its behavior.
Upon launch, the service instantly notifies us about malicious activity and informs us that the system has been infected with Agent Tesla, a widespread malware family that lets criminals steal sensitive information and spy on their victims.
To complete our analysis, we can download and share a detailed threat report with colleagues to let them know about the danger and collect indicators of compromise (IOCs) to improve the organization’s threat detection capabilities.
Wrapping up
As you can see, spearphishing is a high-risk threat to an organization’s security, mainly due to its highly targeted and personalized tactics. But with the right tools at hand, the risk can be minimized.
Using tools like the interactive sandbox ANY.RUN can provide actionable insights, as shown in our real-world example of analyzing a spearphishing attack. It’s an essential part of modern cybersecurity efforts that can help in quickly understanding and mitigating threats.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
Detect malware in seconds
Interact with samples in real time
Save time and money on sandbox setup and maintenance
Record and study all aspects of malware behavior
Collaborate with your team
Scale as you need
The post What is Spearphishing: Definition, Techniques, Real-world Example appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More