How to Analyze Malware in ANY.RUN Sandbox: Eric Parker’s Guide
Recently, Eric Parker, a cybersecurity expert and YouTuber, released a new video on ANY.RUN’s interactive sandbox. We recommend you take a look at his tutorial, as it offers a step-by-step guide on how to use the service and save time on reverse engineering.
Here’s our overview of the key highlights from the video.
About malware analysis in a sandbox
Sandboxing is a crucial process in cybersecurity that lets professionals analyze malware in a controlled environment. Sandboxes provide a safe space to upload and examine potentially malicious samples without compromising your actual system.
ANY.RUN’s sandbox offers interactive analysis, providing users with a real-time view of how malware behaves and allowing them to engage with the system and samples just like on a standard computer.
Setting up a sandbox environment
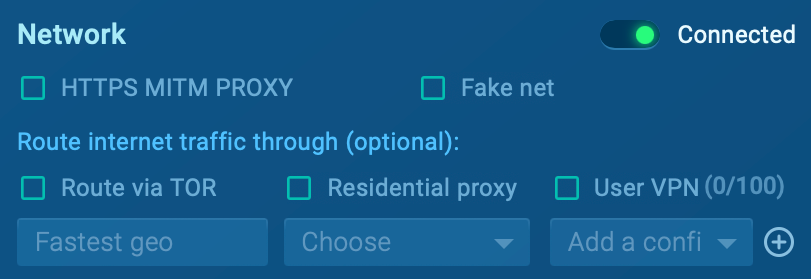
Eric began by highlighting various settings of ANY.RUN that can be adjusted for different scenarios, including:
MITM Proxy: This setting is particularly useful for intercepting and analyzing network traffic, such as HTTP requests made by the malware. This allows you to track how the malware communicates with command and control (C2) servers and gather more detailed information about its actions.
FakeNet: This option is effective if you’re worried about malware with worm-like capabilities, allowing detection of network shares or interactions with non-functional command and control servers.
Learn more about MITM proxy and FakeNet
Operating System Customization: ANY.RUN offers a variety of OS options, from older versions of Windows (7/32-bit, 7/64-bit) to the latest Windows 11. Linux users can also run samples for cross-platform analysis.
For legacy malware, using an older OS might be necessary for full compatibility. Eric recommends experimenting with different OS options based on the malware sample.
Pre-installed soft set: You can choose pre-installed software sets, such as Office or Complete, to simulate real-world environments, making the analysis more realistic. Users can also upload their own tools to the virtual machine for quick access during the investigation.
Privacy Settings: You can choose whether your analysis results are public or private. If you’re working with sensitive malware samples that could contain proprietary information, this feature ensures confidentiality.
Duration Control: For malware that delays execution (e.g., with sleep functions), you can extend the sandbox runtime to capture the full scope of its behavior.
Sandbox analysis of Zombie malware
In the video demonstration, Eric uploaded a malware sample he suspected of being malware. ANY.RUN’s sandbox quickly identified warning signs, detecting file replacements and abnormal behaviors indicative of malware infection.
Key points in the analysis:
File overwriting: The malware replaced files with an executable payload. In the example, the malicious EXE was found to overwrite legitimate system files and create numerous temporary files.
File dumping: One of ANY.RUN’s most valuable features was the ability to dump files mid-execution, making it easier to analyze malware that uses packing or encryption to conceal its malicious actions.
Executable identification: Uploading the file to the sandbox made it possible to instantly identify it as malicious and belonging to the Zombie malware family.
Analysis of Pysilon Discord RAT
Eric emphasized that the goal of any malware analyst is not to understand every line of code, but to get a good view of how the program interacts with the system. This is where an interactive sandbox can prove extremely helpful.
By running the malware in a virtual environment, analysts can quickly understand its behavior without delving into advanced reverse engineering.
In many cases, dynamic analysis alone can provide all the necessary information, bypassing the need for a full static analysis. Eric showed this by running a Pysilon Discord RAT sample in the sandbox.
Pysilon is a malware that is often packed in a unique way, making static analysis more difficult. To avoid dealing with the packer, Eric simply enabled the MITM proxy in ANY.RUN, which allowed him to acquire the malware’s Discord bot token in a few seconds.
ANY.RUN also identified a newly spawned executable named “driveinst.exe” which mimicked a legitimate process. This executable was flagged as unsigned, raising a red flag.
ANY.RUN automatically categorized the malware as a stealer, highlighting its malicious actions and network communications.
As a result, the bot token was captured, the malware’s behavior was observed, and the analysis was completed in less than 30 seconds.
Conclusion
Sandboxes, as demonstrated by Eric Parker, are a powerful tool in the fight against malware. Sandbox analysis allowed Eric to extract crucial information within minutes, cutting down the time needed for manual reverse engineering.
The sandbox provided live data on network traffic, file manipulation, and system changes, delivering instant feedback on malware behavior.
Eric was able to avoid the need to manually unpack or decrypt files, streamlining the analysis process.
To see full potential of ANY.RUN’s sandbox, request a 14-day free trial →
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
The post How to Analyze Malware in ANY.RUN Sandbox: Eric Parker’s Guide appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More