Letters with Remcos RAT hosted in Discord | Kaspersky official blog
Since the beginning of the summer, Kaspersky systems have been recording an increase in the detection of Remcos remote-access trojan attacks. The probable reason for this is a wave of malicious emails in which attackers try to convince employees of various companies to click on a link for malware installation.
Malicious letters
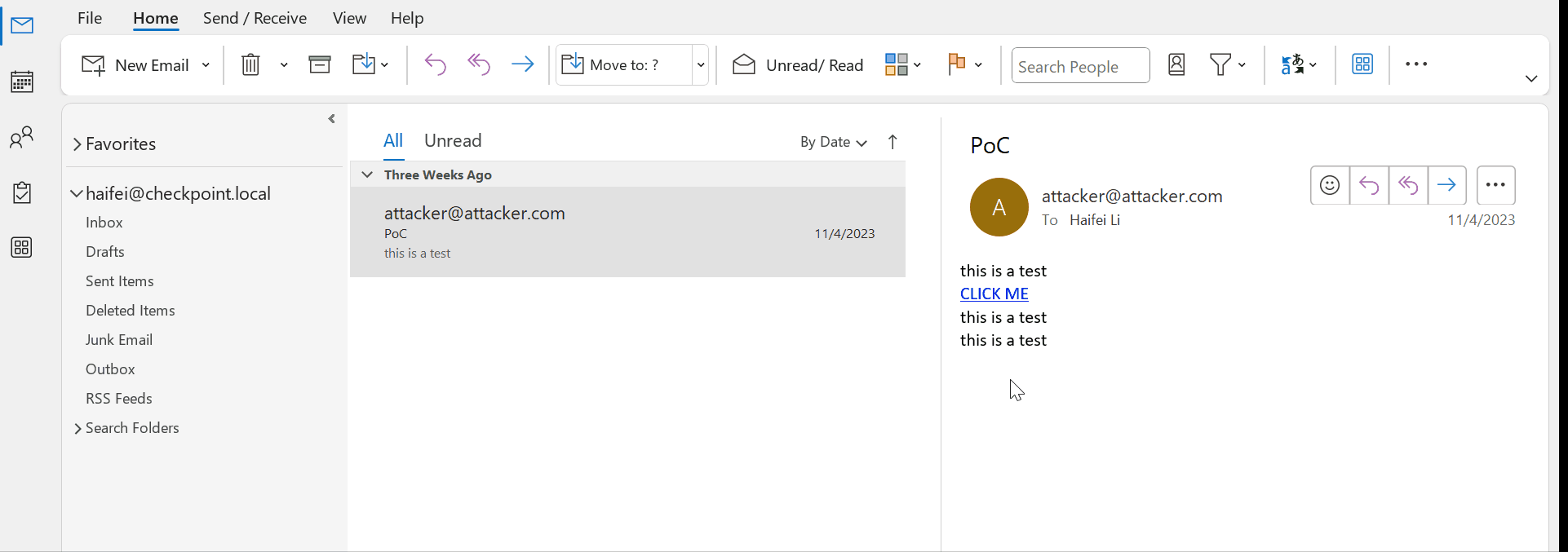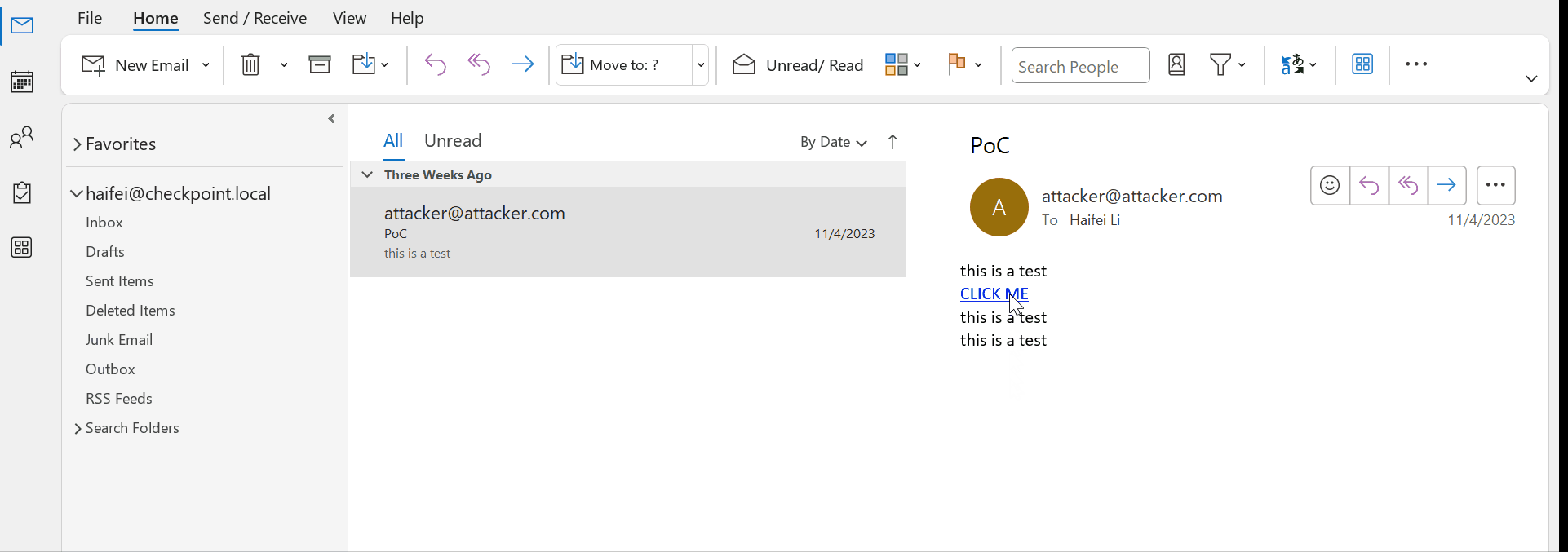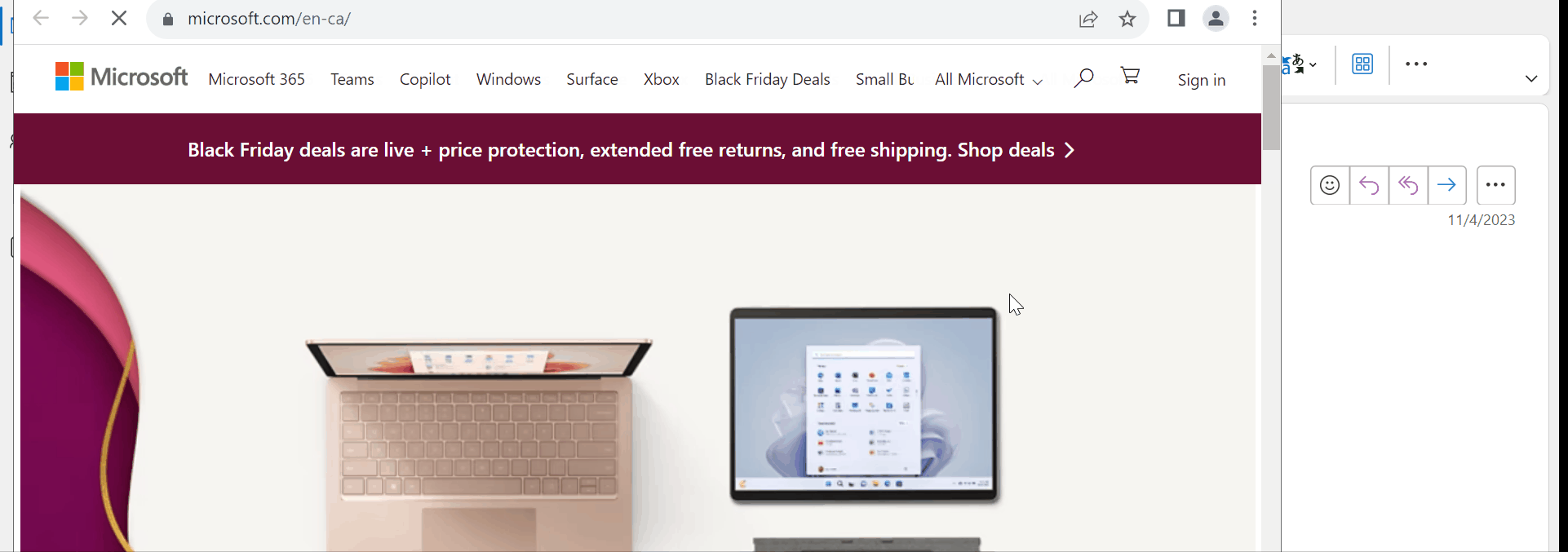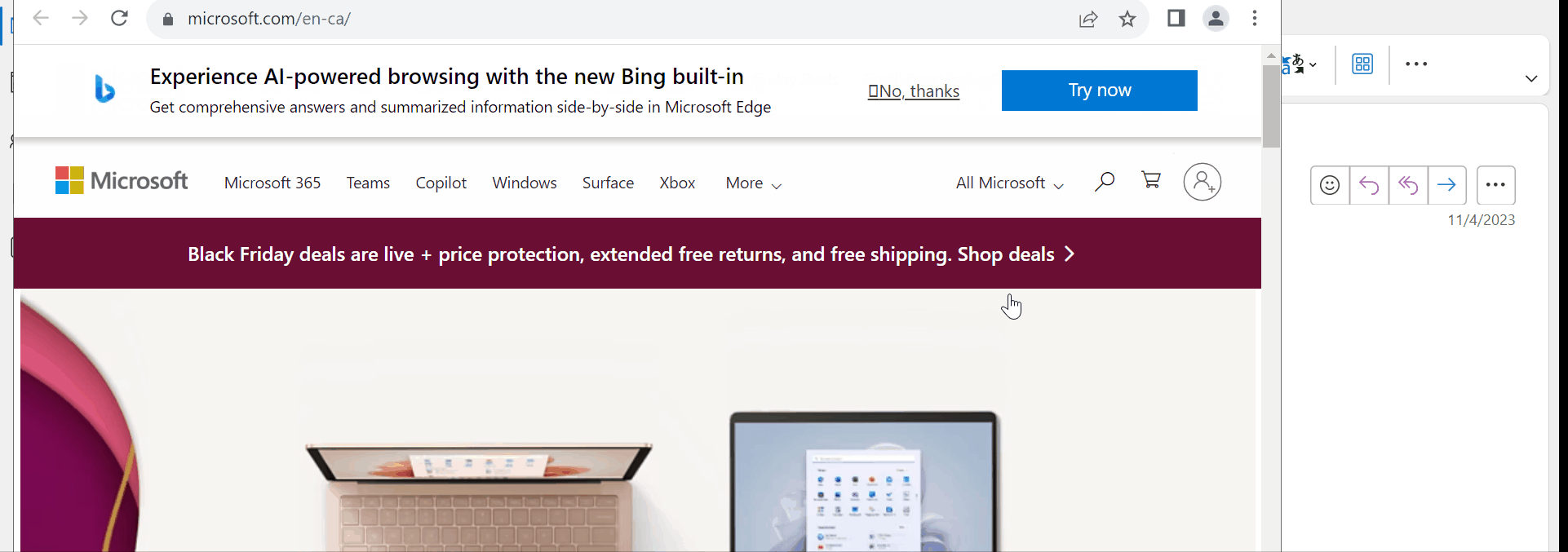
The bait that the attackers are using in this mailout isn’t something extraordinary. They pose as a new client who wants to purchase some products or services and tries to clarify some information: the availability or prices of some merchandise, their compliance with some criteria, or something similar. What matters is that, in order to clarify the information, the recipient must click the link and read the list of these criteria or requirements. To make their letters more persuasive, cybercriminals often ask how quickly it will be possible to deliver the goods or ask about terms for international delivery. Of course, you shouldn’t follow the link — it doesn’t lead to a list, but to a malicious script.
The attackers store their malicious script in an interesting place. Links have the address that looks like https://cdn.discordapp.com/attachments/. Discord is a completely legitimate communication platform, which allows users to exchange instant messages, make audio and video calls, and, most importantly, send various files. A Discord user can click on any file sent through this application and get a link that will make it available to an external user (this is necessary, for example, to quickly share a file via another messenger). It is these links that look like https://cdn.discordapp.com/attachments/ with some set of numbers identifying a specific file.
Discord is actively used by various gaming communities, but it’s sometimes also used by companies to communicate within different teams and departments or even with customers. Therefore, systems that filter malicious content in emails often don’t consider links to files stored on Discord servers as suspicious.
Accordingly, if a recipient of the letter decides to follow such a link, he’ll in fact download malicious JavaScript that imitates a text file. When the victim opens this file, malicious script will launch powershell which, in turn, will download the Remcos RAT to the user’s computer.
What is Remcos RAT and how dangerous is it?
Theoretically, Remcos RAT — or Remote Control and Surveillance — is a program for remote administration, which was released by the company Breaking Security. But it has long been used by cybercriminals for espionage and taking control of computers running Windows. For example, in 2020, we wrote about the use of Remcos RAT in malicious mailings that exploited the common delays in deliveries of goods during the coronavirus pandemic.
Remcos RAT collects data about both the victim and their computer, and then serves as a backdoor through which attackers can take complete control of the system. They download additional malicious software and run it, collect account data, record logs of user activity, and so on.
How to stay safe
In order to ensure that the Remcos malware doesn’t harm your company, we recommend using reliable security solutions both at the level of the mail gateway and on all work devices that have access to the internet. Thus, the malicious emails will be detected before they reach the mailboxes of employees, but even if attackers come up with a new delivery method, our endpoint protection solutions won’t let to download it. Kaspersky Endpoint Security detects Remcos RAT as Backdoor.MSIL.Remcos or Backdoor.Win32.Remcos.
Kaspersky official blog – Read More