Google Tracked 75 Zero-Days in 2024
The number of exploited zero-days seen by Google in 2024 dropped to 75, from 98 observed in the previous year.
The post Google Tracked 75 Zero-Days in 2024 appeared first on SecurityWeek.
SecurityWeek – Read More
The number of exploited zero-days seen by Google in 2024 dropped to 75, from 98 observed in the previous year.
The post Google Tracked 75 Zero-Days in 2024 appeared first on SecurityWeek.
SecurityWeek – Read More
More than 30 companies announced a total of $1.7 billion in funding in weeks leading up to the industry’s largest gathering.
The post Cybersecurity Firms Raise Over $1.7 Billion Ahead of RSA Conference 2025 appeared first on SecurityWeek.
SecurityWeek – Read More
Browser security firm LayerX has raised $11 million in a Series A funding round extension led by Jump Capital.
The post LayerX Raises $11 Million for Browser Security Solution appeared first on SecurityWeek.
SecurityWeek – Read More
More than 400 SAP NetWeaver servers are impacted by CVE-2025-31324, an exploited remote code execution vulnerability.
The post Exploited Vulnerability Exposes Over 400 SAP NetWeaver Servers to Attacks appeared first on SecurityWeek.
SecurityWeek – Read More
Hundreds of companies are showcasing their products and services this week at the 2025 edition of the RSA Conference in San Francisco.
The post RSA Conference 2025 Announcements Summary (Day 1) appeared first on SecurityWeek.
SecurityWeek – Read More
The number of vulnerabilities exploited by attacks may not be growing these days, but they are increasingly affecting enterprise technologies.
darkreading – Read More
Governments like China and North Korea, along with spyware makers, used the most recorded zero-days in 2024.
Security News | TechCrunch – Read More
CISA urges immediate patching for recently disclosed Broadcom, Commvault, and Qualitia vulnerabilities exploited in the wild.
The post CISA Warns of Exploited Broadcom, Commvault Vulnerabilities appeared first on SecurityWeek.
SecurityWeek – Read More
In a new campaign detected in March 2025, senior members of the World Uyghur Congress (WUC) living in exile have been targeted by a Windows-based malware that’s capable of conducting surveillance.
The spear-phishing campaign involved the use of a trojanized version of a legitimate open-source word processing and spell check tool called UyghurEdit++ developed to support the use of the Uyghur
The Hacker News – Read More
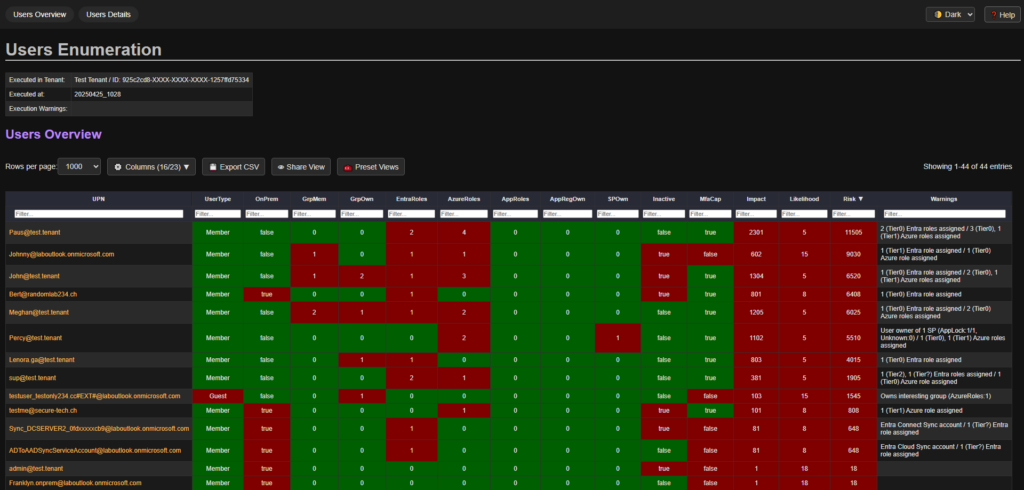
TL;DR: PowerShell tool to enumerate Entra ID objects, assignments and identify highly privileged objects or risky configurations.
Entra ID environments can contain thousands of objects – users, groups, service principals, and more – each with unique properties and complex relationships. While manual reviews through the Entra portal might be feasible in smaller environments, they become a tedious task in larger, complex environments.
There are already several free tools available for enumerating Entra ID data. However, some of them typically focus only on dumping data, without offering much support for identifying highly privileged objects or potentially risky object configurations. Other tools do not enumerate certain objects, properties or assignments like Administrative Units, Application app lock configurations, M365 groups or Privileged Identity Management (PIM) eligible assignments.
This is why we built EntraFalcon, a PowerShell tool designed to help security analysts, penetration testers, and sysadmins review Entra ID environments. It highlights potentially risky object configurations and privileged assignments that are often overlooked.
Key Features
Example Findings
Some examples EntraFalcon helps to identify:
Report Samples
Required Permissions
To collect data from Entra ID, the user executing the tool requires at least Global Reader permissions.
To include Azure IAM data (optional but recommended), the Reader role is needed for each relevant Management Group or Subscription.
Limitations
While EntraFalcon helps surface potential issues, manual analysis is still essential to fully understand the impact of each finding. Furthermore, the risk scores provided are intended as indicators, not definitive assessments – they should be reviewed in context as part of a broader investigation.
Get Started
To get started with EntraFalcon, visit our GitHub repository for usage instructions, examples, and additional details.
Compass Security Blog – Read More