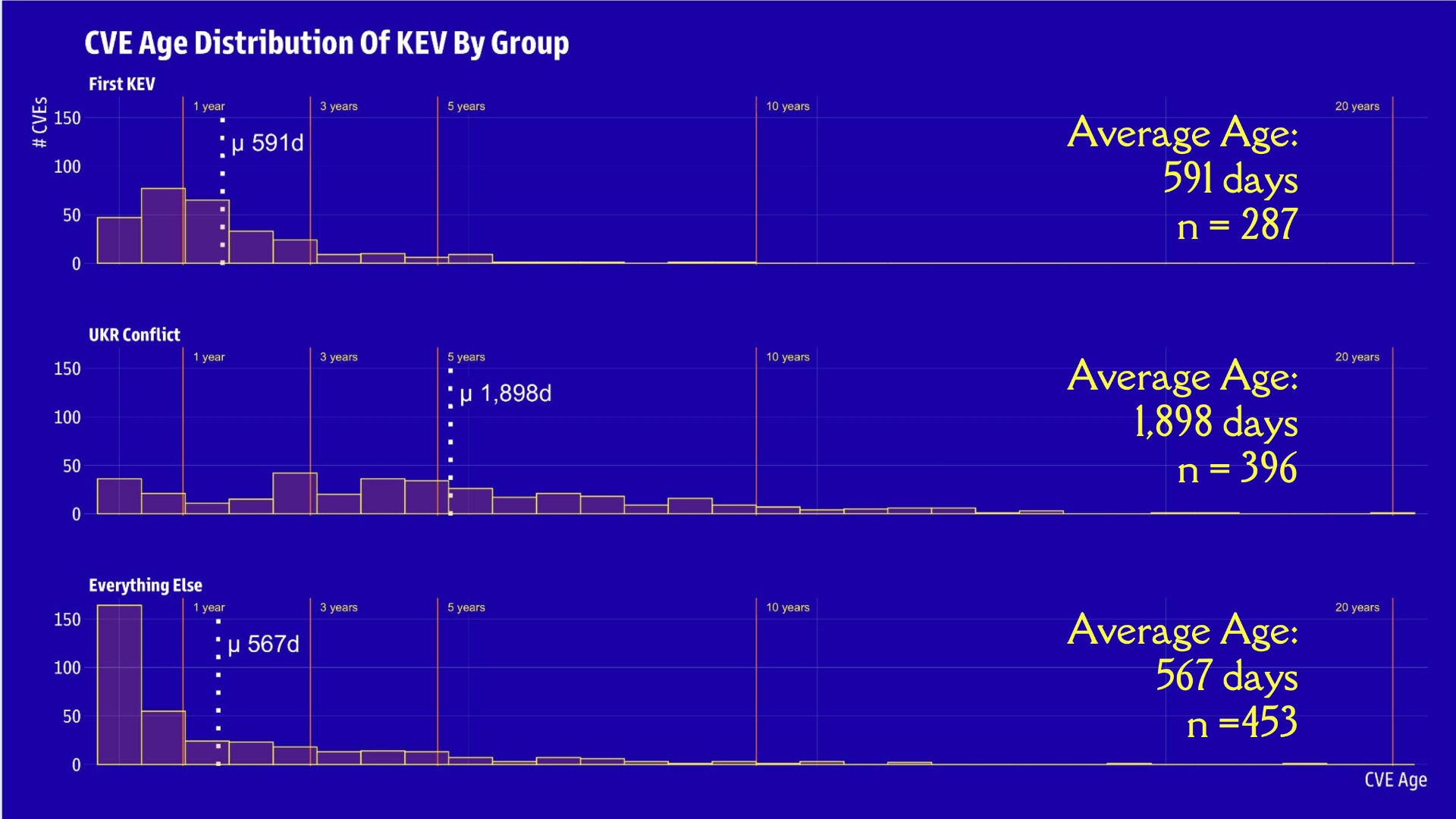
Monitoring Changes in KEV List Can Guide Security Teams
The number of additions to the Known Exploited Vulnerabilities catalog is growing quickly, but even silent changes to already-documented flaws can help security teams prioritize.
darkreading – Read More